Competition document: autonomy and big data for defence
Updated 12 October 2015
1. Autonomy and big data for defence
The Centre for Defence Enterprise (CDE) presents this SBRI themed competition in association with UKDSC, as part of the Defence Growth Partnership (DGP) Innovation Challenge.
This competition aims to address the challenges associated with the adoption of autonomy and big data in defence. We want proof-of-concept research proposals for innovative component technologies and techniques to acquire, process, visualise and analyse data that can be used to support decision making for both human and autonomous systems. Proposals can relate to any military environment, in the air, on land or at sea.
This competition was briefed at the CDE Innovation Network event on 21 October 2015 and at a webinar on 3 November 2015.
Your proposal must be received by CDE by 5pm on Wednesday 11 November 2015. Submit your proposal using the CDE online portal.
2. Background
The amount of data both required and produced by defence systems and processes is rapidly increasing and becoming more difficult to manage. In a time when military manpower is limited, manual processing of data is too time consuming. The use of autonomous systems and processes to make sense of data to support decision making could increase efficiency and reduce the risk and cost of operations.
Big data is a data set that is too large and complex to manage and process with standard methods or tools. This could be due to high data volume (amount of data), velocity (speed of data in and out) or variety (range of data types and sources). These issues apply equally for defence and commercial data. Given the nature of the military decisions that have to be made, it’s of extreme importance that we understand the quality of the data and the value each piece of data brings.
Proposals to this CDE themed competition must demonstrate a defence benefit and should be capable of being integrated with existing systems to offer a comprehensive capability. Proposals can address one challenge or a number of challenges. We invite research proposals that draw from emerging ideas, across the widest range of market sectors.
3. Technology challenges
3.1 Challenge 1: acquiring data for autonomous vehicles
The majority of autonomous systems being developed, particularly in civil applications, rely on comprehensive, detailed terrain and environmental data, known as ‘prior knowledge’. Locally sensed data is added to this for their navigation and safe operations.
MOD will need to use autonomous vehicles in complex environments in the air, on land and at sea where there’s limited or out-of-date prior knowledge about the terrain or environment. The autonomous vehicles will have on-board sensors but these may be limited by the need to be covert or to operate in harsh electro-magnetic environments, eg GPS degraded or denied environments.
We’re looking for novel data collection methods (sensors, algorithms etc), which take in existing data from various sources, including potentially new sources or existing sources used in a novel way.
We’re also looking for methods for gathering data from on board the autonomous vehicle, so that the data can be combined to allow effective and safe operation.
What we want
In challenge 1, we’re looking for methods of:
-
acquiring prior knowledge of environments to allow effective and safe operation of autonomous air, land, or sea vehicles
-
processing data sets to simplify or enable their use by autonomous vehicles
-
exploiting prior knowledge to achieve greater levels of autonomy
You should consider that the technologies may need to operate in complex and hostile environments, be used remotely or covertly, and at short notice.
We’re interested in technologies that allow a vehicle to:
- automatically select the best route in a complex and rapidly changing environment, eg due to the weather or battlespace activity
- use passive rather than active sensors
- operate without GPS
- operate over extended ranges eg beyond visual line of sight communications
What we don’t want
In challenge 1, we’re not looking for:
- platform technologies, eg airframes, propulsion
- architectures
- intent or threat profiling
3.2 Challenge 2: sourcing big data in difficult environments
In any deployed task group, the command platform can be overwhelmed by data from various sources.
When operating in a remote, isolated location in a hostile environment there’s a need to establish a high degree of confidence in the data received. Data for tactical decision making will need to be rapidly brought together from various sources and collection methods. Resources to address this, in terms of both computing and manpower, can be limited. Bandwidth limitations will affect the speed of accessing external data and there’ll be occasional loss of access to individual external data sources. Firewalls and other security restrictions may also limit data and information access.
Without relying on well-connected data centres, MOD will need to check data collected in a tactical environment against all the information available. This will be challenging due to the volume, variety and speed of the data, and the fact that it may not be known what data exists.
MOD will need to assign priorities and understand what’s critical to the mission. Given the diversity and sensitivity of some of the data sources, the security and integrity of the wider data sources will need to be maintained.
What we want
In challenge 2, we’re looking for proposals for technologies that allow storage, indexing, search, discovery, retrieval and visualisation of data collected that don’t rely on well-connected data centres.
Proposals should also consider the authentication and security aspects of the data queries.
3.3 Challenge 3: validating sources of big data
Data sources will include known, trusted and classified sources as well as ambiguous or unknown, and unvalidated open sources. The combination of this data to support decision making will require a confidence level or reliability score to be assigned.
This will also allow examination for audit, legal or ethical reasons, especially in circumstances where the rules of engagement for data collection and use may be dynamic. This requirement ranges from source validation, fact checking and confirmation, copyright assurance, through to protection of personal data and reputation management.
What we want
In challenge 3, we want proposals to develop novel tools, techniques, and procedures that combine data resources with metadata, or similar ‘tag’ constructs.
These should clearly and concisely frame the way in which the underlying data may be considered, placed into context, and used.
Proposals should consider the methods that the analytical, and other, components will use to interact with, and account for, the tagged data.
3.4 Challenge 4: managing and visualising big data
New persistent surveillance systems will produce significant volumes of data, likely to overwhelm the specialist surveillance analysts processing the data at intelligence centres.
The problem is even more difficult when there are multiple, diverse sensor feeds from the same or multiple persistent surveillance systems. Many information types can be involved, ranging from traditional intelligence surveillance and reconnaissance (ISR) sources through to open-source and social media.
This can be solved by 2 approaches: near real-time processing close to or at the sensor, and post-processing analysis close to, or at, the analyst.
What we want
In challenge 4, we want proposals that develop novel tools, techniques and procedures to autonomously process, infer meaning from, and distribute information so that analysts aren’t overwhelmed by the data.
Given the complexity of this challenge, and the requirement for short-duration phase-1 proposals in this competition, we expect proposals to focus on component technologies or processes rather than address the challenge as a whole.
4. Exploitation
This CDE themed competition is split into 2 phases:
-
Phase-1 projects will be up to 6 months in duration and seek technologies at a component level (phase-1 projects must complete by 30 June 2016).
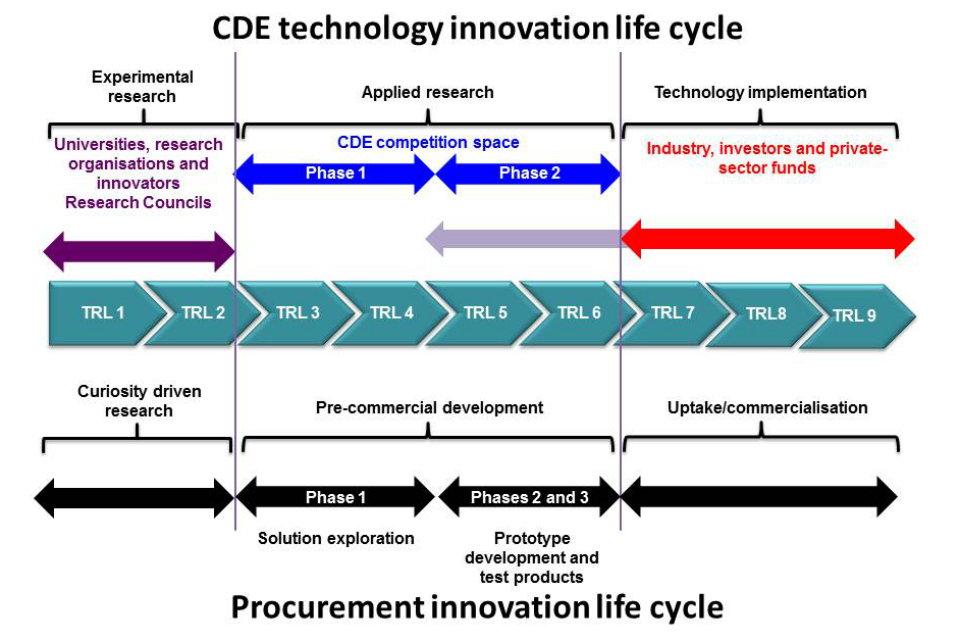
Up to £2 million will be made available for phase 1 and funding will be considered on a per-project basis. We anticipate that a number of phase-1 projects will be funded from a range of suppliers. Phase-1 projects should produce outputs within the pre-commercial development, solution exploration stage of the innovation life cycle at least at technology readiness level (TRL) 3 to 4. -
Following assessment and down-selection of the phase-2 proposals, a number of successful phase-1 projects may be taken forward with a second stage of investment.
This will be for a further 6 months and outputs are anticipated to be within the pre-commercial procurement, prototype development stage of the innovation life cycle, at around TRL 5 to 6.
The aim of phase-2 projects will be to integrate several phase-1 outputs into systems that can be demonstrated in a realistic environment. Successful bidders may therefore be expected to collaborate to deliver phase-2 objectives.
At least £2 million will be made available for this second phase and funding will be considered on a per-project basis.
Phase-1 projects producing a successful output may be offered accelerated development through the commercialisation phase by UKDSC to enhance the potential for exploitation.
The diagram below shows the technology innovation life cycle, how this maps with TRLs and where this CDE competition fits in. For a description of TRLs access MOD’s Acquisition System Guidance.
5. Important information
This competition will be supported by presentations given at the Innovation Network event on Wednesday 21 October 2015.
Proposals for funding must be received by CDE by 5pm on Wednesday 11 November 2015 using the CDE online portal.
You must mark your proposals to this themed competition with ‘autonomy and big data for defence’ plus ‘challenge 1, 2, 3 or 4’ as appropriate as a prefix in your title. You can submit a single proposal offering a solution to meet more than one challenge.
Proposals must include:
- a clearly defined, cost-effective, and achievable research programme
- outputs with the potential to deliver innovative or disruptive capabilities
- practical proof-of-concept demonstrations
An ideal proposal should include:
- a consideration of systems and implementation issues
- outputs with well-defined, ideally open, interfaces to allow ready integration with other components
- a clear view of potential exploitation routes
- recommendations and proposals for future technical development beyond phase 1
Phase-1 proposals will be up to 6 months in duration; projects must be completed by 30 June 2016.
In this CDE themed competition we’re not looking for:
- paper-based studies
- enterprise-level solutions (a laptop is at the high end of processing power)
- marginal improvements in capability
- solutions that offer no significant defence and security benefit
- technology watch or horizon scanning
- roadmaps or technology prediction
- demonstrations of existing technology products
Read important information on what all CDE proposals must include.
There’s no cap on the value of proposals, however it’s more likely that at phase 1 a larger number of lower-value proposals (up to £100,000) will be funded. At phase 2, it’s likely that a small number of the successful phase-1 proposals will be funded to a higher value.
Successful proposals will be 100% funded.
Suppliers should note that Dstl won’t provide data sets, equipment or information to support the development, testing or refinement of proposed projects. Suppliers must either supply their own or use relevant third-party data sets to demonstrate how their proposals are relevant.
Proposals will be assessed by subject matter experts from UKDSC (working under a non-disclosure agreement), MOD and Dstl using the MOD Performance Assessment Framework (PAF).
Collaboration often strengthens a proposal so we welcome joint proposals from academia or small and medium-sized enterprises and larger companies. One of the collaborators must act as the lead so that MOD can contract with a single entity.
Each project will be assigned a technical partner in Dstl who’ll provide the interface between the project and the defence and security community and will assist in developing potential routes to exploitation within this community as appropriate. Subject matter experts from UKDSC will be available to companies throughout phases 1 and 2 of the competition to maximize the opportunity for exploitation of projects.
Deliverables from contracts will be made available to Dstl technical partners and are subject to review by UK MOD. UKDSC won’t automatically have rights of use of the deliverables, but each funded proposer will have the opportunity to engage with UKDSC to enhance the likelihood of exploitation of their technology. This is likely to take the form of confidential face-to-face meetings and marketplace-style events to provide an opportunity for successful proposers to demonstrate capability to MOD, UKDSC, and UK and international defence customers.
6. Dates
| 21 October 2015 | Competition briefing at Innovation Network event |
| 3 November 2015 | Webinar |
| 11 November 2015 | Competition closes at 5pm |
| Early January 2016 | Contract placement initiated and feedback provided |
| 30 June 2016 | Latest date for the delivery of phase-1 proof-of-concept research |
| July 2016 | Marketplace event |
| July 2016 | Phase-2 funding decisions made |
| 31 March 2017 | Phase-2 contracts complete |
7. Queries and help
While you’re preparing your proposals, you can contact us if you have any queries: [email protected]
Capacity to answer these queries is limited in terms of volume and scope. Queries should be limited to a few simple questions or if provided with a short (few paragraphs) description of your proposal, the technical team will provide, without commitment or prejudice, broad yes/no answers. This query facility is not to be used for extensive technical discussions, detailed review of proposals or supporting the iterative development of ideas. While all reasonable efforts will be made to answer queries, CDE and Dstl reserves the right to impose management controls when higher than average volumes of queries or resource demands restrict fair access to all potential proposal submitters.
