Identification Document Validation Technology
Published 28 March 2018
Part 1: Introduction to identity document validation technology
Identity document validation technologies (IDVT) are forms of technology that can quickly and easily assist you to establish the authenticity of documents presented for identity verification purposes, including:
- passports
- biometric residence permits
- driving licences
- identity cards
IDVTs can play an important role in preventing the use of fraudulent documentation. Whilst they do not replace forgery experts, they provide higher levels of accuracy and assurance than the manual checking of documents by staff not used to checking different forms of identity documents.
1.1 What forms of technology do they use?
There are many forms of IDVTs to suit the different needs of users. These consist of the following parts:
-
A device to scan the identity document – these include specialised passport and ID card readers, smartphones, webcams, and flatbed scanners to capture an image of the document, some of which can also read chipped documents.
-
Software and a template library of identity documents – the software checks the security features contained on the document and compares the image of the document against a template stored in the library. Algorithms are used to draw together the results of the checks and score them to indicate whether an identity document is authentic.
Images of different types of identity document validation systems
Some systems can also:
- conduct checks against other data-sources – some systems are able to conduct checks against other data sources, which can be used by the system to help verify an identity
- perform impostor checks – some systems incorporate biometric checking capabilities or other forms of technology to help prevent genuine documents from being used by impostors
- be included as part of a wider identity checking service – some IDVTs are included as part of a wider digital service where identity documents need to be checked, such as online applications to the Disclosure and Barring Service (DBS)[footnote 1]
- maintain secure digital records of identity documents they have checked – some IDVTs enable users to reduce their levels of paper processing and the costs of storing paper documents
- inform individuals about what data is being sought and enable them to consent and to provide an audit trail for both the individual and the relying party
1.2 Who might want to use IDVT?
Any organisation or individual who wants to verify an identity as part of a document checking process to determine whether the person is eligible to:
- obtain employment or accommodation in the UK, as part of a right to work or right to rent check
- work in vulnerable sectors, e.g. where an individual requires a DBS check
- obtain access to controlled premises or services, such as secure areas or licensed premises
- apply for public services
- be charged for receiving NHS treatment
- obtain financial services
- receive other goods and services
This list is not exhaustive and there are many other circumstances when identity documentation needs to be checked and validated.
1.3 Why use IDVTs?
There is a wide range of documents that individuals can use to establish their identity and status, for example passports, identity cards and driving licences. When high quality forgeries are presented to users who are not familiar with the quality of documents, it can become challenging for them to differentiate between genuine and false documents.
IDVTs are tools that can help you to save:
- time – identity document validation technology should make checking documents quick
- money – should reduce the risk of employing or providing accommodation to illegal migrants or becoming victims of fraud
- worry – it should provide higher levels of confidence about the identity of prospective applicants, users of services, customers or employees
1.4 Remote checking
Many IDVTs are able to validate identity documents remotely by enabling your clients to upload their own identity documents and facial images using their own technology such as smartphones, webcams and flatbed scanners. This offers significant improvements beyond accepting unverified copies of documents or relying upon third parties, to conduct checks on identity documents. They could enable pre-recruitment sifting, although this would not constitute a right to work check.
1.5 In-person checks
You may need to see individuals in person (which can include over Skype) and examine their original identity documents, for example to meet legal requirements, such as checking individuals’ right to work in the UK. In this situation IDVTs can provide more effective checks on identity documents than basic visual inspections by users with little or no training in examining identity documents.
Although this technology, if used properly, can be a powerful tool, it should only be used as part of the overall checking process on identity documents. The technology does not replace the need to follow the Home Office’s guidance on examining identity documents.
Part 2 – Choosing the right Identity Document Validation Technology
Identity Document Validation Technology (IDVT) comes in various forms, with different capabilities and costs. You will need to assess the levels of assurances that are acceptable for your business or organisation by taking account of:
- the risks you need to manage
- the costs of the system
- the numbers of identity documents that you anticipate that you will need to check
You will also need to be clear about your particular requirements when choosing what types of systems to procure, including where and how you will use the technology.
2.1 Elements of a document check
There are 3 elements of a document check:
- checking whether a document is genuine – many false identity documents look real to untrained individuals who are required to check documents. IDVTs make it easier to authenticate them
- Identity Document validation – even when a document is genuine, it is not possible to confirm whether or not it has been cancelled following theft or loss. Many IDVTs are able to make checks against other databases, such as Interpol’s lost and stolen passport data
- linking the holder to the document – it is often hard to match document holders to the photograph on identity documents. Sometimes the document holder’s image will have altered, for example if their hair style and colour changes. Many IDTVs include facial matching technology to enable the person checking the document to link it to the holder.
All IDVTs will check whether a document is genuine, but many systems also include checks against relevant data sources and incorporate facial matching technology to link the document to the holder.
2.2 Evaluating the types of IDVTs to meet particular needs
As a general rule, IDVTs that perform a wide range of checks are likely to offer higher levels of assurance. The systems that offer the highest levels of assurance will include features such as having the capability to validate chipped documents, to scan documents under different light sources and make checks against other sources of data. The number and range of checks IDVTs can perform will depend on the type of device used to scan the documents, the document libraries and security features that are checked and the levels of access to other data sources. The checking of identity documents forms part of your overall checks towards verifying an identity.
Different users are likely to have distinct requirements in terms of the levels of assurance (LoA)[footnote 2] they require when performing checks on identity documents. These range from LoA Level 1 where there is no requirement for the identity of the individual to be proven, up to Level 4 where the person’s identity needs to be strongly protected against impersonation or fabrication, such as for those persons who may be in a position of trust, or situations where compromise could represent a danger to life.
The table below provides examples of circumstances where different assurance levels are required.
| Rank | Levels of Assurance (LoA) | Types of checks that may be undertaken | Examples of purposes for conducting checks |
|---|---|---|---|
| 4 | For position of trust and for situations where any compromise could represent a significant danger to life. | Conducts many checks on identity document security features. Compares a multi-spectrum scan of an identity document against an identity document template library. Opens and inspects a chipped document. Conducts checks against a range of other data sources. Undertakes biometric checks against the features stored on the document. | Employment in a critical industry or at a site of critical infrastructure, e.g. an airport; |
| 3 | Assurance based on beyond reasonable doubt. | Conducts many checks on identity document security features. Compares a scan of an identity document against an identity document template library. Opens and inspects a chipped document. Conducts checks against a range of other data sources. Undertakes impostor checks. | Where there is a need to protect vulnerable people, such as children or the elderly. Where employers need to ensure their employees are trustworthy, e.g. contract cleaners and security staff. When necessary to protect a business’s or organisation’s reputation. |
| 2 | Assurance based upon balance of probabilities. | Conducts checks on identity document security features. Compares a scan of an identity document against an identity document template library. Conducts checks against other data sources. | Conducting a right to work check using a photographic document. Undertaking a right to rent check using a photographic document. When conducting “know your customer” anti-money laundering checks. To meet licensing requirements. |
| 1 | No requirement to prove the identity of the document holder. | Simple manual check. | Collecting a parcel from the Post Office. |
Different identity document checking systems provide different levels of assurance. Here is a list of the systems we know to be currently available, in order of most to least assurance.
- Devices with advanced document security, including capability to scan document under different forms of light, library of templates of documents, feature checks, checks against databases, chip reading and impostor checks using biometrics
- Devices with document security feature checks, chip reading, checks against databases and imposter checks
- Devices with document security checks and checks against databases
- Devices with document security feature checks
- Manual check
- No check
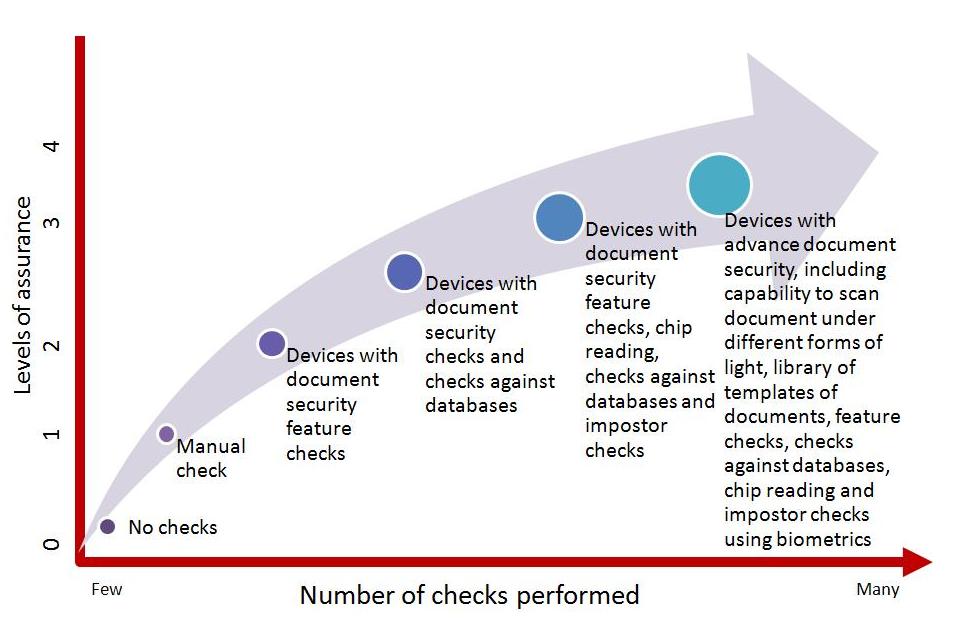
A representative comparison of identity document validation technology and assurance levels
2.3 What you should consider when procuring IDVTs
You need to understand the capabilities of any system that you are considering procuring. All IDVTs should be capable of doing all or some of the following:
- detect counterfeit[footnote 3]documents (all) – you should expect document validation systems to detect counterfeit documents. However, not all services are able to detect counterfeits to the same level of accuracy. Some services will offer more secure checks than others. Basic checks usually involve checking whether the biographic information contained on the document matches the Machine Readable Zone (MRZ) which is printed on the bottom of the biographical page in modern passports and on some identity cards. The more sophisticated technologies have the ability to open and examine chips on passports and identity cards and are able to scan images of documents under different forms of light
- detect forged [footnote 4] documents (some) – not all document validation systems will be able to detect forged documents, because some parts of the document will be genuine
- authenticate chipped documents (some) – some IDVTs, including many apps available on some smartphone devices that contain a Near Field Communication (NFC) chip reading capability[footnote 5], can authenticate the chips on biometric (electronic) passports or identity cards. Documents that contain chips containing biometric features which can be electronically authenticated will include the symbol on the face of the document. This supports secure biometric checks on the document holder against the image stored on the chip
- operate either in a fully or semi-automated manner (some) – many IDVTs are fully or semi-automated so that the system either confirms whether the document is authentic or provides a report to enable the user to come to a decision on whether to accept the document as authentic
- not to be destructive to the document being checked (all) – IDVTs should be able to check documents repeatedly without damaging them. This means the check should not involve the physical testing of the document
- provide a report of each check to the user (all) – the IDVT should be able to provide a clear report of its check to the user so it is clear how it verified a document and can be shared with law enforcement bodies where appropriate
- operate as an online service if required (some) – the IDVT should be able to operate as an online service, where required by the user, so they are able to remotely share and update information. Not all users will want or need to share data outside their organisations and will require updates through other means
- meets the requirements of General Data Protection Regulation (all) – the IDVT will need to ensure their services meet the requirements of this regulation which will come into force from May 2018
In addition to the IDVT, many of the providers include additional services so that they are able to:
- share reports on fraudulent documents, (including images and meta-data) with other databases. For example, through the Metropolitan Police Service Amberhill database[footnote 6] on false identities and identity documents
- securely store any data that needs to be retained on the system. This will be helpful when it is essential for users to keep records of any checks they have made
- provide a support service to the user (digital or telephone) where users can query suspect documents. This helps users to confirm the authenticity of suspect documents and what they should do with false documents
- create local watch lists and, enable users to share watch lists among their user groups. For example, licensed premises may want to share data on individuals who they have excluded from their premises, or employers may want to share the data on false documents with other branches or franchises
- offer data minimisation capabilities. For example, licensed premises only need to know whether a person is aged over the age of 18 or older. Door staff should not have access to other non-relevant information such as the individual’s address, date of birth, passport number and expiry date
2.4 The parts of Identity Document Validation Technology (IDVT)
IDVTs consist of 2 main parts:
- a device to scan an image (and a chip if available) of the identity document
- software to check the security features and compare the image of the identity document against a template.
Many systems will also have capabilities to make checks against a range of databases and procedures to prevent identity documents from being misused by impostors.
You will need to consider how you want to check identity documents. The first stage is to consider where and how you intend the identity documents to be scanned. This will depend on whether the document holder is required to attend a location in person with their original document or whether you want the document holder to be able to remotely upload their identity documents onto the system themselves.
Devices for taking an image of the identity document
Identity documents can be scanned onto the system using specialist passport readers, smartphones, webcams or flatbed scanners. The types of devices required to scan the identity documents will depend on the purpose of the document check. Many service providers back up the technologies used to scan identity documents by including remote teams of security experts who have additional facial recognition and document reviewing skills to help conduct further examinations on suspect documents.
Specialist passport / identity card readers
These are specialist identity document readers which are specially designed to scan passports and identity cards. The devices that offer the fullest range of checks should be able to conduct high quality scans of passports and identity documents under optical, ultra-violet (UV) and infrared light and read chipped documents, such as biometric passports.
These devices are often used as part of a bespoke identity document scanning system such as where there is a need to conduct high volumes of document checks and/ or where you require very high levels of assurance on the documents and the individuals you want to check. These systems can be specially made to meet specific purposes, for example they may be found at licensed premises, at air and seaports, in the form of e-gates, and by employers and businesses that check large numbers of identity documents.
Smartphones
IDVTs that embrace smartphone technology are not reliant on any hardware beyond the user’s own smartphone device. They can greatly improve your levels of assurance, particularly in situations where your organisation has multiple-sites, divisions, outlets, many people conducting identity document checks or where you need to provide self-uploading services to individuals whose identity documents you need to validate.
Smartphones with Near Field Communication (NFC)[footnote 7] capability are able to conduct checks on chipped documents. However, unlike some specialist passport readers, they currently are only able to view documents under visible[footnote 8] light, although they can inform consumers when light quality is insufficient. Software for smartphones is developing the sophistication to review holograms on identity documents and detect against a variety of spoofing attacks.
Webcam/flatbed scanner validation systems[footnote 9]
These are ideal if you do not need to conduct frequent checks and do not require the same levels of assurance that a specialist passport reader may offer. Like smartphones, webcams and flatbed scanners are widely available and offer users a wide range of opportunities to check identity documents or enable individuals to self-upload their own identity documents.
At present, webcams and flatbed scanners can only view documents under visible light and are unlikely to incorporate NFC readers to be able to check chipped documents. However, you can purchase a separate NFC chip reading device.
Identity document examination software and document libraries
After an identity document has been scanned, information is taken from the document for analysis by the IDVT. The number of checks on an identity document that the system will be able to perform will depend upon the type of device used to scan the document, whether the system is able to access a library of document templates and its ability to open the chips on biometric identity documents.
Most IDVTs will conduct checks on the MRZ printed on the identity document, but more advanced systems incorporate software that enables them to conduct a wide range of checks on the security features contained on identity documents. Many systems incorporate checks against a document template to assess whether they match what is expected on a genuine document, including under different light sources.
The results of these different checks are brought together to provide the document examiner with an assessment on the validity of the document being checked. Some IDVTs will provide a simple binary (yes/no) response on the authenticity of the identity document whereas other systems will provide a report on the document and leave the decision to the examiner.
Additional capabilities
Many IDVTs are also able to conduct other checks to help verify the identities of holders of identity documents and to link them to the document.
Checks against other sources of data
Many IDVTs are able to conduct checks against other sources of data, either through customisable Application Programming Interfaces (API) or through other means. This enables the examiner to build a picture of the individual whose identity they want to check.
Measures to identify impostors
Several IDVTs include measures to detect impostors. These may include the use of biometrics or other means to identify impostors, such as shared secrets or via other means. This allows the examiner to link the identity document to the holder.
2.5 Types of documents that IDVTs may be able to check
There are some circumstances when you may be mandated by law to conduct checks on identity documents. Many IDVTs can assist employers and landlords to conduct right to work or right to rent checks, provided they are able to check identity documents specified in List A and List B contained in the right to work checklist or the right to rent checklist, and their use is consistent with the prescribed processes for conducting the checks. In addition, where a Disclosure and Barring Service (DBS) check is needed, the IDVT should include identity documents listed in Group 1, Group 2a and Group 2b of the Disclosure and Barring Service document check-list published on Gov.UK.
The Cabinet Office has also published guidance on Identity Proofing and Verification of an Individual which can be found on Gov.UK, which includes details of identity documents that can be used to help establish an identity.
You may also require the IDVT to be able to check other forms of identity documents and should check with the service provider whether their system is able to check such documents.
2.6 IDVTs can be integrated into other services
Many IDVTs are used for purposes beyond validating identity documents and form part of a wider product or service. These services can include:
Integrated right to work and rent services
Many providers incorporate IDVTs into their digital right to work and right to rent checking services, so that not only do their systems validate the identity documents being used, but also support the whole checking process including by keeping records of individuals’ status which can help evidence compliance with Home Office regulations. Some Registered Bodies use IDVTs to enable identity documents to be validated as part of a digital application service for an enhanced DBS check.
Other uses
There are service providers that use IDVTs as part of a pre-screening measure or as part of an application for another document, for instance when applying for a security pass.
2.7 Current limitations on using IDVTs
IDVTs are useful tools for checking identity documentation. They may not identify some of the more sophisticated forgeries or photo substitutions. Many service providers militate against this by including remote teams of document and facial recognition experts. More basic services are unlikely to identify imposters (lookalikes), who make up a considerable portion of individuals involved in document abuse.
IDVTs are not intended to replace the use of trained forgery officers, nor should they be used to replace existing systems that your business or organisation have in place to tackle fraud.
The use of IDVTs does not replace published checking processes that you must conduct in order to meet statutory requirements, such as for right to work and right to rent checks. For example, if you are required to check original documents in the presence of the document holder, using IDVT will help you to identify fraudulent documents, but they will not replace your obligation to check documents in accordance with requirements set out in Home Office regulations. Under the current law[footnote 10], using IDVTs to conduct right to work checks cannot guarantee that employers or landlords will not receive a civil penalty for employing an illegal migrant. Employers and landlords can establish a statutory excuse (a defence) against a civil penalty under Home Office regulations without having to rely on this technology. However, if used correctly in accordance with the providers’ instructions, IDVTs are a valuable tool for identifying fraudulent identity documentation.
Part 3 - How to use Identity Document Validation Technology
This part of the guidance is intended to help you to get the best out of any identity document validation technology (IDVT) that you have selected to use. It is intended to supplement the instructions provided by your IDVT provider.
3.1 Training
The type of training your IDVT provider offers you will depend on the type of IDVT you have chosen. Where the service provider is required to install specialist hardware they may provide you with training at your location. IDVT providers which utilise your own hardware, such as smartphones normally provide remote online training that may include step-by-step guidance as part of their service.
3.2 Using the IDVT
You must ensure that you use IDVTs in an appropriate manner so that you only use the minimum amount of data as necessary to help you to make a decision. Any data retained must be secured safely and must not be used beyond its intended purpose without the identity document holder’s consent, except for the purposes of the prevention, detection and prosecution of crime or where the law requires you to keep the data.
3.3 Informing holders of identity documents on the use of IDVTs
When you use an IDVT you should make it clear to your customers, prospective employees and tenants that you conduct checks on identity documents using an IDVT and with whom you will share details of suspected fraudulent identity documentation, such as the police, Immigration Enforcement or other organisations where it is lawful to so.
You should also provide the individuals with information on how their data may be processed. This can be done through the use of a fair processing notice ideally as a separate notice or if included as part of guidance or terms and conditions at a location where it is easily seen and not buried in the text.
An example of a fair processing notice is set out below:
[Name of business/ licensed premises/ public authority] uses identity document validation technology to assess the authenticity of identity documents provided to it in connection with [an application for [employment/ rental accommodation/ benefit etc;], [seeking entry to this licensed premise]. The identity document validation system will only retain relevant personal data provided in connection [with the application/ request to enter this licensed premise]. Data taken from the identity document you provided for this [application, request] will only be used and retained in accordance to the Data Protection Act 1998 or other relevant legislation. However, data relating to suspected fraudulent documentation may be shared with the document validation system provider for further analysis and with any relevant law enforcement body such as the police and Immigration Enforcement. Possession and use of fraudulent documents may constitute an offence under the Identity Documents Act 2010, which can result in a sentence of imprisonment of up to ten years.
You should adapt the notice to meet your particular requirements.
3.4 Electronic reports of fraudulent documentation
Where your IDVT is capable of sharing data on false documents you should consider transmitting reports of any identity document that the IDVT indicates to be fraudulent to the Metropolitan Police Service (Amberhill) database. This database draws together data relating to fraudulent identity documents. Before you send the report to Amberhill you should allow the document to be rescanned and you should contact your IDVT’s support service, where available, for advice to ensure the document was correctly analysed by the system.
When the police receive data through Amberhill which it identifies as evidence of false or fraudulent documentation, the police will treat it as a crime in action. This data is cross-checked against other databases to identify fraud and deception in both the public and private sectors.
Amberhill data is currently available to some public and private sector organisations, such as CIFAS (a not-for-profit company working to protect businesses, charities, public bodies and individuals from financial crime), the Disclosure and Barring Service (DBS) and some IDVT providers. Following the introduction of the General Data Protection Regulation (GDPR) and the Law Enforcement Directive, there will need to be a suitable data processing contract in place between the IDVT provider and Amberhill which will define the nature of the data that is to be exchanged, the processing to be undertaken, and the security, and any other measures to be adhered to by the data processor.
Some IDVTs enable you to share reports on suspicious identity documents automatically or semi-automatically with Amberhill. However, you can also e-mail the reports to [email protected] in a PDF format so the police can add it to the database. Where you suspect that you may be the victim of fraud, you should also report the matter to Action Fraud. Where an immigration crime is suspected the report should be uploaded on to Report an Immigration Crime in a PDF format.
3.5 Conducting checks on original documents
When conducting checks on original identity documents, you should initially perform a physical check of the identity document. In doing so, you will find it useful to follow the National Document Fraud Unit’s (NDFU) Guidance on examining identity documents, although you are not legally required to have regard to this guidance.
Most identity documentation will use similar types of security features, which can be checked using the following basic equipment (especially if you do not have access to an IDVT which includes specialist passport readers that can check identity documents using ultraviolet (UV) and infrared light):
- Magnifying glass of at least 10x magnification; and
- UV light source – NDFU recommends that the UV light-source uses a wavelength of 365nm, which is sometimes referred to as “black-light”
Low quality counterfeit documents will often fluoresce (shine or glow brightly) when held under a UV light source. While you are not obliged to obtain such equipment, it will assist you to carry out physical checks on documents more effectively.
Where the holder is present
Where a document holder presents a document which appears to be fraudulent, there are a number of possible courses of action open to you. You should not put yourself at risk of harm and should return any suspicious documents to the holder if they request the return of their documents, unless you consider it safe to retain them. Only law enforcement officers such as a police constable or an immigration officer have formal legal powers to seize documents which they suspect to be fraudulent, although members of the public may act where appropriate to prevent crime.
Where the document holder is present, and you prefer to return the documents to the person, you should forward a copy of the fraudulent document plus any additional details to the police or Home Office Immigration Enforcement. Alternatively, you might want to ask the individual’s permission to retain the document to enable you to conduct further checks. When the holder leaves the original document in your possession you should send it to your local police or Immigration, Compliance and Enforcement team office, and include a copy of the report provided by the IDVT and inform the person who presented the document.
Suspected impostors
Many IDVTs now include the capability to conduct impostor checks, such as using biometrics. You may come across genuine identity documents being used by impostors. These may include lost or stolen documents, or documents that have been lent to the impostor by the rightful holder.
When you suspect a document holder to be an impostor you should ask the individual whether they have any other forms of identity documentation that should help them to confirm their identity. The NDFU guidance includes a section on spotting impostors. You should try to obtain copies of all identification documents used by the suspected impostor. When you have significant doubts on the holder’s identity, you should report this to the police in the first instance.
Handling suspicious documents
When you involve the police or Home Office Immigration Enforcement, you should hand over to the officers any copies or original documentation you have retained, and provide them with any print outs from the IDVT, giving as much detail on the individual as possible along with a copy of the report on the suspicious document. You may also be required to provide a witness statement to support any arrest and/or prosecution.
3.6 Where you do not see the holder or their identity documents in person
In circumstances where identity document holders are able to self-upload their documents on to an IDVT and it is unable to validate their identity documents, you will need to consider how you manage the situation with the individual. You should allow document holders another opportunity to upload their identity document or ask them to upload an alternative identity document.
Depending on your reasons for requiring evidence of an individual’s identity, you may want to offer the person an alternative means to enable them to establish their identity. You may want the person to participate in an online video interview where there are concerns on the validity of a document.
In some circumstances you might want to ask individuals to attend an event in person with their original documentation or allow them to submit their original documents to enable the user to check them physically. Alternatively, you could choose to deny them a service until they are able to provide adequate identity documentation.
Where you suspect that the identity documents may be fraudulent, you should inform the police or Immigration Enforcement as soon as possible. The IDVT’s report on any suspicious identity document should be referred to Amberhill. Any original identity documents obtained from the holder, which you suspect to be fraudulent, should be referred to your local police or Immigration, Compliance and Enforcement Team office.
3.7 Dealing with false alerts
Occasionally IDVTs will provide false alerts. This might be as a result of a poor scan, a damaged document or the device being used to read the document being used in an unsuitable location, for example where it is too dark or too light.
Genuine documents reported as false documents
When an IDVT indicates that a document may be fraudulent, you might want to allow the document to be rescanned to see whether the IDVT provides the same response. Where you are in possession of the original document, you should also conduct a physical check of the document using the guidance published by NDFU. You may want to ask the document holder to provide an alternative identity document. Ultimately, it is your responsibility to decide whether to accept a document as genuine.
You are strongly advised to make use of any support service provided as part of the IDVT service to help resolve any issues concerning the document, such as dealing with a dirty document or adding a new genuine document to the IDVT provider’s document template library.
Fraudulent documents reported as genuine
There may be some instances where the IDVT reports a fraudulent document to be genuine. Often this is where a genuine document has been cleverly forged. When you have access to the original document you are advised to conduct a physical check using the NDFU guidance. Gov.UK enables employers to check the validity of biometric residence permits (BRP) and PRADO includes links to enable some EU documents to be validated.
Where you suspect a document which the IDVT has validated as genuine to be fraudulent, you should inform the IDVT provider to enable them to research why its system failed to identify the document. You should also refer the identity document to Amberhill.
3.8 Legal advice on the use of Identity Document Validation Systems and suspected fraudulent information
The Information Commissioner’s Office (ICO) has confirmed that there are no legal barriers to the sharing of fraudulent document data identified through the use of IDVTs as long as you have adequate data handling procedures in place and that the information is only being shared for a specific purpose, namely for the prevention and detection of crime and/or immigration abuses. This includes using IDVTs to prevent individuals from using false identities for criminal or illegal immigration purposes. Crime prevention through collaboration by improving data sharing is encouraged.
Although fraudulent identity data is not covered by the Data Protection Act 1998, you will still need to ensure you have systems in place to comply with the requirements of the Act (and the new Data Protection Bill based on the GDPR that will replace it). The presentation of a specified fraudulent identity document within the meaning of the Identity Documents Act 2010 is a crime. In effect, where a fraudulent identity from a document has been captured, relaying that information to the police or Immigration Enforcement is equivalent to reporting the facts of a crime or abuse of immigration laws.
You should only use IDVTs in a manner that is proportionate to the purpose for which you intend it to be used, including the reducing the threat of crime and immigration abuse, to comply with legislation covering data management. You can do this by putting measures in place to ensure that:
- you can assess the IDVT to ensure it meets the intended purposes (see Part 2 - Choosing the right Identity Document Validation Technology)
- staff using the equipment are given the appropriate training on its use
- you can restrict access to the IDVT records and analysis to those whose duties require it
- there is an audit and access-logging function, which enables tracking of the users who have accessed the data
- where the IDVT is capable of automatically sharing data on fraudulent identity documents with law enforcement, that the service provider has a data sharing agreement in place with them
- the IDVT provider has measures in place to reduce the risk of its technology being misused
- thresholds for what would be identified as a false identity document are set to an appropriate standard, so that the system does not produce too many false positive or negative results
- where scanned data contains details of hijacked identities, Amberhill will help to manage the impact on the genuine owner of that identity where possible
- unless recorded data needs to be retained for a specific purpose, for example as evidence of a Right-to-Work or Right-to-Rent check, you should be able to delete data in accordance with local data policies that enable you to comply with relevant legislation on data retention
Where the police or Immigration Enforcement assess the document to be a genuine UK issued document, whether falsified or fraudulently obtained, they are responsible for returning it to the issuing authority. Where original foreign documents have been retained on the grounds of being fraudulent, these should be sent to Immigration Enforcement to either return to the mission of the issuing country or used to support the removal of a foreign national from the UK.
Part 4 – Identity Document Validation Technology: how to protect it from misuse
Identity Document Validation Technologies (IDVT) are a powerful tool designed to prevent identity document abuse. However, there is a risk that they could be misused when there are insufficient safeguards to prevent the technology falling into the hands of criminals and those seeking to facilitate immigration crime.
In response to similar threats, the suppliers of specialist printers worked with the Metropolitan Police Service and introduced a code of practice to prevent specialist printers being obtained by criminals to produce fraudulent identity documents.
4.1 Good practice to prevent misuse
IDVT providers should consider adopting the following measures to prevent the misuse of their technology and systems:
Record Keeping
Maintain and retain proper records of all transactions on the supply of IDVTs for both UK and overseas customers.
Customer Profiling
To profile new customers as set out in Annex A.
Supply of technology/ applications
Not to supply or provide IDVT services where there are any serious doubts on the legitimacy of the customer or on the intended use of the technology.
Any concerns about new customers can be reported to the Metropolitan Police Service “Amberhill” or a similar law enforcement/Government led central repository for false identity data.
Data management
IDVT systems must enable data to be used and retained in a manner that is compliant with data protection legislation, including the Data Protection Bill based on the General Data Protection Regulation (GDPR) that will be in force from May 2018. Users will want to ensure that their use of IDVT services complies with current and future data protection legislation. In particular, users will want to understand what happens to data taken from the scanned identity documents and the access IDVT providers will have to such information.
IDVT providers should be aware that if any personal data captured from identity documents is to be stored outside of the EEA, e.g. in the cloud[footnote 11], they must have suitable measures in place to comply with Principle 8 of the DPA (or equivalent provisions of the GDPR or legislation based on it).
Annex A: profile of potential indicators of fraud
The following characteristics may indicate possible intention to use identity document verification systems fraudulently:
- the potential client’s address does not tally with the telephone number given.
- the potential customer does not supply a company name/headed paper. This may indicate that they are unable to provide verification that they are a legitimate representative of the company.
- the potential customer is unwilling to supply a contact address.
- the potential customer supplies an address that is a serviced office.
- the potential customer supplies an address that is a residential address.
- the potential customer supplies an address which is actually a house for sale. This can be checked through websites such as zoopla.com and rightmove.co.uk. However, not being listed on one of these websites does not confirm that a house is NOT for sale.
- the potential customer gives details that do not match the website of the business that they purport to represent.
- the potential customer supplies a telephone number that does not work when you ring it back.
- the potential customer is only able to supply a mobile telephone number.
- the potential customer supplies a telephone number beginning with ‘070’ - this is a premium rate platform telephone number and is known to be favoured by criminals.
- the request from the potential customer comes from an email domain that does not match that of the real company.
- the potential customer purports to be from a company that does not have a valid credit reference or fails an identity verification check. This check can be carried out via a credit reference agency which would charge per enquiry or on an annual contract. This would be usual when setting up a new customer account or potential new dealer, especially where a credit account is requested or anticipated.
- the potential customer purports to be from a company that is not registered with Companies House, or when checking with Companies House the details do not match. For example, the age of the company and directors’ names are not correct, the registered office address and registered company number given are not correct, or the company is not trading. The name and home address of at least one director could also be verified, as well as trade and bank references. Where the potential customer is an individual, the home address and trading address could be verified. Basic information can be obtained free of charge through the WebCheck service
- the potential customer asks to pay a large amount in cash, and if so, is this normal behaviour?
- the potential customer asks to collect the equipment personally, and if so, is this normal behaviour?
- the potential customer wants business equipment/supplies delivered to a non-business address.
- the potential customer asks for the equipment urgently, without good reason. This may indicate that the buyer is attempting to buy the equipment or materials using a compromised credit card with a limited lifespan.
- the potential customer does not ask for receipts/invoices.
- the potential customer does not want a contract for repairs/servicing, and is this normal behaviour?
- the potential customer does not attempt to negotiate over the price, and is this normal behaviour?
These fraud indicators may not be of a significant cause for concern on their own, but combined with others may represent an indicator of potential fraud.
Glossary of terms
| Application Programming Interface (API) | A set of functions and procedures that allow the creation of applications which access the features or data of an operating system, application, or other service. |
|---|---|
| Cloud | Cloud computing is a type of Internet-based computing that provides shared computer processing resources and data to computers and other devices on demand. |
| Counterfeit | A complete reproduction from scratch to resemble an officially issued document. |
| Document scanner | A form of identity document validation system, which is an integrated system that enables identity documents to be scanned and validated. |
| Forgery | A genuine document that has been unlawfully altered in some way. |
| Identity document validation technology | The software and the devices used to validate identity documents, including any systems and the overall service. |
| Know your customer | The process of a business identifying and verifying the identity of its clients. |
| Passport reader | A specialised device for examining passports and identity cards. |
| Right to rent | The checking process that landlords, homeowners and letting agents need to conduct to confirm whether a person can rent accommodation. |
| Right to work | The process for checking whether a potential employee has the right to work in the UK and the types of documents employers should check. |
| Validation | A process performed to determine whether a piece of Identity Evidence is Genuine and/or Valid. |
| Verification | A process performed to determine whether the Applicant is the owner of the Claimed Identity. |
-
The Disclosure and Barring Service (DBS) helps employers make safer recruitment decisions and prevent unsuitable people from working with vulnerable groups, including children. It replaces the Criminal Records Bureau (CRB) and Independent Safeguarding Authority (ISA). ↩
-
Details on assurance levels can be found in chapter 4 of the Cabinet Office Good Practice Guidance 45 ↩
-
A counterfeit is a complete reproduction from scratch to resemble an officially issued document. ↩
-
A forged document consists of genuine document(s) that have been altered – e.g. substitution of a page(s), photograph or alteration of personal details ↩
-
For a list of NFC phones go to NFC World. However, Apple iPhones do not currently support chip-reading beyond Apple Pay. ↩
-
A database held by the Metropolitan Police Service relating to fraudulent identity documents ↩
-
ISO/IEC 14443 Type A and Type B ↩
-
This is optical light that can be seen by the human eye. ↩
-
Webcam/ flatbed scanners should be able to capture images from documents to a quality of at least 300dpi. ↩
-
The Immigration (Restrictions on Employment) Order 2007 as amended by the Immigration (Restrictions on Employment) (Codes of Practice and Amendment) Order 2014 ↩
-
A type of Internet-based computing that provides shared computer processing resources and data to devices on demand. ↩
