Countering vehicle as a weapon: best practice guidance for goods vehicle operators and drivers
Published 6 August 2019
Foreword
The modern world can feel like an increasingly dangerous place. The use of vehicles as a weapon to injure and kill people has become a real threat, which means people who operate and drive commercial vehicles need to act. It is vital that transport businesses adopt a responsible approach to security. The agencies, which are charged with protecting all members of society, have identified some simple and inexpensive procedures to assist operators, transport managers and drivers. That is why I am pleased to endorse the Department for Transport’s industry specific best practice guidance.
The guidance outlines the steps you can take to help keep the public and your organisation safe from attack.
The guidance covers:
- security culture – including pre-employment checks for staff and drivers
- site security – including vehicle access and operating centres
- vehicle security – including checking vehicles and what to do if a vehicle is taken
It also contains a top 10 list of actions for commercial vehicle drivers.
Our key message is for you and your employees to take security as seriously as you take safety.
Richard Turfitt, Senior Traffic Commissioner for Great Britain
Section 1 – Introduction
Purpose of this guidance
This guidance sets out straightforward steps that can help mitigate the threat of goods vehicles being used in vehicle as a weapon attack.
As well as helping to keep the public safe by deterring would-be attackers from using your fleet, following this advice will:
- help prevent acts of terrorism
- help protect your organisation’s reputation
- demonstrate your commitment to Corporate Social Responsibility
- help to improve security culture within your business
- help reduce crime
The guidance covers security measures for:
- building and embedding a positive security culture and behaviours
- personnel security
- operating centres and maintenance facilities
- transport managers and drivers
- vehicles
- general security issues
The guidance sets out simple steps Transport Operators should take to promote a good security culture in their organisation and help keep drivers, sites and vehicles secure.
Links to a wide range of more detailed official guidance.
Remember, good security = good business
What is a Goods Vehicle?
For this guidance, the term ‘Goods Vehicle’ applies to a vehicle designed to carry goods or materials rather than passengers, from a small van to a large lorry.
What is a Vehicle as A Weapon attack?
A vehicle can be used as a weapon intentionally to injure and kill people. This is referred to as a ‘vehicle as a weapon (VAW) attack’.
VAW is a low complexity methodology requiring little or no training. With a plentiful source of vehicles on UK roads, it is therefore within the capability of individuals to try and steal one and use it in an attack.
Crowded public spaces are targeted by this type of attack. There are a range of online terrorist and extremist materials aimed at inspiring terrorists to carry out VAW attacks and previous attacks have encouraged copycats, who now see VAW as a successful means to cause terror. Lorries and vans pose an increased risk if used in VAW attacks because of their size, profile and weight, all of which increase the potential impact.
This is a real threat: there have been numerous VAW attacks in the UK and around the world in recent years, killing and injuring hundreds of innocent people.
Consequently, VAW remains a likely attack methodology for the foreseeable future.
Following this guidance will help reduce the possibility of one of your vehicles being used as a weapon.
Section 2 – People, security culture and behaviours
What is a security culture?
A strong security culture will help mitigate security risks, including VAW by promoting compliance with security measures, awareness and vigilance.
The benefits of an effective security culture are:
- a workforce that is more likely to be engaged with, and take responsibility for, security issues
- increased compliance with protective security measures, such as those set out in this guidance
- reduced risk of insider incidents
- awareness of the most relevant security threats
- employees are more likely to think and act in a security-conscious manner
Security behaviours in your organisation
A strong security culture will promote positive security behaviours across your workforce.
Using the Centre for the Protection of National Infrastructure (CPNI) 5Es framework (Educate, Enable, Shape the Environment, Encourage the Action and Evaluate the Impact) an organisation can embed and sustain security behaviours within their workforce.
The CPNI ‘Embedding Security Behaviours: using the 5Es Framework’ document provides guidance on how to implement the 5Es within an organisation .
Vigilance and reporting suspicious behaviour
In an emergency always ring 999. Security awareness, vigilance and reporting suspicious behaviour, increases the likelihood that people with hostile intentions will be detected or deterred.
Employee vigilance complements other elements of protective security (PDF, 1.8MB).
Procedures for reporting any unusual behaviour to supervisors and police, should be developed and briefed to all staff.
We recommend reporting any concerns via the National Counter Terrorism Policing (NCTPHQ) Action Counters Terrorism (ACT) campaign:
‘If you’ve seen or heard something that could suggest a terrorist threat to the UK do not ignore it, report it’.
Report suspicious activity to the police by calling confidentially on 0800 789 321 or through the report in confidence service on the page: https://act.campaign.gov.uk.
The public already contribute intelligence to around a third of the most serious terrorism investigations. Staff should be reassured that they need not be concerned about wasting police time or getting someone into trouble.
Due to the nature of security operations you may not hear back from the Police, this does not mean they have ignored you concerns.
Vigilance will be further promoted by putting in place systems for recording site security patrols, monitoring and checking visitors and vehicles.
Identification passes should be issued to staff and visitors and worn at all times. All staff should be encouraged to challenge anyone on your premises who is not wearing a pass.
Company security plan
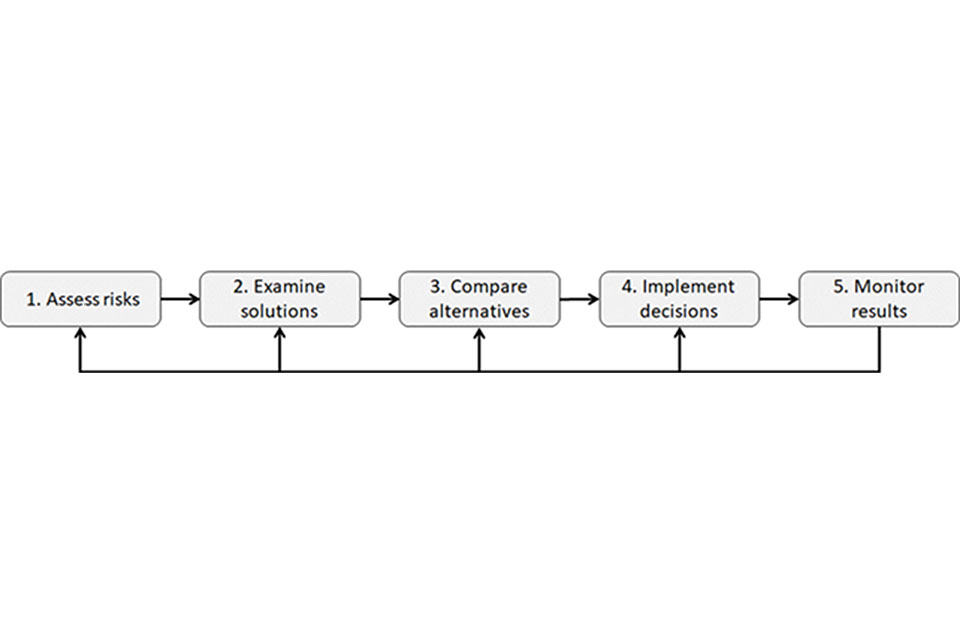
A security plan is the cornerstone of a secure goods vehicle operation that sets the basis for strong security behaviours, culture and security practice.
A company security plan should cover at least the following steps, themes and elements:
- allocate security responsibilities to a staff member who has appropriate authority to make security-related decisions and implement them
- assess risks posed by your vehicle operations. Involve key business partners including customers, shippers, freight forwarders, carriers, security service providers, and insurance experts in the risk assessment, if possible. Define and understand the security risks in vehicle operations including the ‘insider threat’
- identify possible solutions that will prevent one of your vehicles being used in an attack, while considering options, for example, that all vehicles should be locked when not in use. Security plans and procedures should be updated regularly. Collect feedback from drivers and consider the drivers’ needs and wishes in day-to-day vehicle security management. When implementing decisions ensure employees have been consulted. Undertake regular reviews to monitor results and progress
- altogether, when designing security plans, managers should consider the five-step model illustrated above which guides them through the most important aspects and themes of goods vehicle security management
Countering the insider threat with pre-employment checks
Insiders with access to your processes and assets can be a source of threat. An insider could be a full time or part-time employee, a contractor or even a business partner. They could deliberately join your organisation to gain access to your organisation’s assets to mount an attack, or they may be triggered to act at some point during their employment.
Organisations should provide a trusted resource for staff to report security concerns or suspicions, either anonymously or otherwise, this is a positive way of nurturing a security culture within an organisation.
Robust pre-employment checks for all employees can help mitigate the insider threat by:
- deterring applicants who may wish to harm your organisation from applying for employment
- detecting individuals with an intent to harm your organisation at the recruitment/application phase
- and denying employment to individuals intending to harm your organisation, and deny employment in roles for which the applicant is unsuitable
Remember: deter - detect - deny
Consideration should be given to using British Standard 7858 (or equivalent) for security screening of employees.
This standard involves conducting basic identity, financial, employment and criminal records checks. We recommend that the following additional steps are taken when employing drivers:
- check a driver’s references and previous employment history (minimum of five years)
- speak to previous employers
- inform applicants that false details on application forms may lead to dismissal
- check driving licences are valid and look for endorsements before you employ someone, and then at six-monthly intervals afterwards. Drivers should tell you of any changes to their licence
- check if the applicant has any prosecutions pending or is waiting for sentencing by a court
- for agency drivers, ensure that the agency has carried out all of these checks including criminal records checks
- and use only reputable recruitment agencies that are affiliated with a recognised UK trade organisation
Section 3 – Site security
Secure sites prevent vehicles being stolen and potentially used in terrorist attacks
Effective security measures at operating centres and maintenance facilities can help to create a controlled environment which will encourage positive security behaviours amongst staff, act as a deterrent and protect from theft and other criminal activity.
Organisations can consult their local Counter Terrorism Security Advisers (CTSAs) to agree a system for reporting and dealing with suspicious vehicle incidents, and liaise with them regarding securing their sites. CTSAs work with businesses and the community to identify and assess sites that may be vulnerable to terrorist or extremist attack. They also work with trade organisations and professional bodies to ensure counter-terrorism protective security advice is incorporated into general crime prevention advice and guidance.
Basic security measures can help to ensure that an item is not concealed onboard a vehicle when in maintenance centres. Having clear signage in place can discourage unwanted access by vehicles and people. Examples of site security measures:
- fit locks or tamper-proof seals to lockers and equipment boxes;
- access to operating centres should be controlled with appropriate security arrangements i.e. fences, gates, security codes;
- vehicle keys should be stored in a secure locker with security codes. Keys should not be left in vehicles or on hooks in the office easily accessible to anyone
Visitors and contractors
All visitors and contractors accessing the premises should be required to report to reception or an individual in authority to notify their arrival.
Visitors should sign-in, be issued visitor passes and have a legitimate reason for their visit. These identification passes should be worn and ‘be visible’ at all times, anyone not wearing a pass should be asked by a member of staff why they are not wearing a pass. Visitors should be escorted at all times when not in public areas.
This process provides audit information, including sign-in/out times and the purpose of the visit, and can be crucial in the event of an emergency evacuation of the premises. Visitors and contractors should be given a security awareness briefing to include:
- where a pass is issued, it should be displayed prominently at all times while they are on the premises
- anyone without a pass or in an unauthorised area will be challenged
- if a vehicle has been parked on-site, any work/parking permits should be displayed prominently in the windscreen
- remind them to be vigilant when on the premises and of what to do if they see a suspicious item or a person acting unusually
- all doors should be properly closed when leaving, particularly doors leading to non-public areas
- “Tailgating” into non-public areas should not be allowed
- worksites and equipment should be secured on leaving
Vehicle access at sites
The movement of any unauthorised vehicles on site should be strictly controlled and ideally prevented
If this is unavoidable, appropriate access controls should be adopted, for example, a parking permit system for staff, visitor and contractor vehicles or allowing pre-arranged deliveries only.
Security controls
All sites with parked vehicles that are not in use should be subject to security controls that include:
- physical access barriers around the site such as walls and fences which should be in good repair and maintained to acceptable standards
- access control measures at all entrances to prevent unauthorised access
- measures to protect vehicles on the site (locking of vehicles, regular patrols, or CCTV cameras to detect and monitor any unauthorised access)
- wherever possible vehicles, trailers and other material should not be parked/placed near or up against the fence, gates and walls as they may be used as climbing aids or cover from view from the CCTV cameras or guard force security patrols.
Operating centres
The movement of any unauthorised vehicles at operating centres should be prevented or strictly controlled with appropriate access control measures.
Transport Operators should consult their local CTSA to agree a system for reporting and dealing with suspicious vehicles, and liaise with them regarding evacuation plans.
Security at Vehicle maintenance facilities
If your vehicles are repaired and maintained off-site you should ensure that the site’s security is appropriate. Maintenance staff, including sub-contractors should be made aware of your company’s vehicle security policies and procedures. The maintenance agreement between the vehicle operator and the vehicle maintenance company should include a duty to secure the vehicles and keys correctly.
CCTV
CCTV is central to most modern security systems.
Its primary purpose is to detect suspicious activity and act as a verification system for other security measures. CCTV can be a single or combination of systems and technologies to form the overall security solution.
We recommend using an electronic detection system assured by CPNI, which can be sourced from the CPNI Catalogue of Security Equipment (CSE). Most of these work on the five-minute rule. This assumes that each part of a perimeter or sensitive asset is viewed by either a guard or CCTV once every five minutes. This limits the potential time for an unauthorised activity and forces an attacker to act rapidly, making them more likely to trigger an electronic detection system.
Unsecure locations
It is not always possible for vehicles to be parked in a secure location when on route.
A driver is a lone worker and it is important they feel safe and secure while working.
If parking in an unsecure location, operators should ensure that drivers satisfy themselves that the following checks are carried out:
- is the vehicle locked with windows closed? Do you have your keys on your person?
- have you activated the vehicles security devices where applicable?
- has anyone followed you, are you being watched?
- if possible, can you keep the vehicle in sight at all times?
- is the area well lit?
- when returning to your vehicle, does it look the same as when you left?
- are there any external factors that you could reasonably predict (e.g. weather) that could disrupt your route?
- does your company know where you are parking?
- are there parking areas recommended by others which they feel are safe and secure?
- do not post your location on social media
- if you are approached or stopped by police, or an authorised public body, only open the cab door window after officers have shown their identification and inform your Transport Operator. If you suspect the individual is not an authorised officer, and they couldn’t produce their warrant card, keep the cab locked and stay in the vehicle, drive to the nearest Police Station or call 999
- be mindful that the only public bodies with legal powers to stop you while driving are the Police, Driver Vehicle and Standards Agency (DVSA), Highways Authorities such as Highways England and those granted Community Safety Accreditation Scheme Powers (CSAS) powers by the Police. If in any doubt, call the Police
Section 4 – Vehicle security
Checking vehicles
Drivers should visually check their vehicle at the beginning and end of their journey.
Also, whenever they leave or return to their vehicle, they should look for any signs that something has been concealed or the vehicle tampered with.
This can be included as part of the required roadworthiness ‘walk around’ check. A security checklist for drivers supports this guidance.
Securing vehicles
Whenever vehicles are left unattended.
For example, at the start and end of a journey, during a comfort break or while parked as securely as possible, drivers should ensure that all the doors and windows are closed, engine switched off and ignition keys are taken with them. For vehicles not requiring ignition keys, drivers should ensure that they secure the vehicle appropriately before leaving (Annex A). Vehicles should not be left unattended with engines running.
Measures to prevent vehicles being taken by criminals or terrorists and used as a weapon include:
- vehicles should not be left unattended at the roadside with the engines running
- ignition keys should not be left in the vehicle while the driver is not present
- operators of vehicles that require the engine running, to operate auxiliary equipment when the driver is not in the cab, should take appropriate measures to ensure against theft of the vehicle; this could include the provision of a second key to lock the cab doors
- alternative security measures should be considered and used for vehicles not requiring an ignition key
- security measures should be put in place at goods vehicle operating centres or other premises to prevent unauthorised access to vehicles
- goods vehicles must be parked as securely as possible
- drivers and/or Goods Vehicle operators should report any concerns about unusual behaviour that occurs on or close to their vehicle
Vehicle security equipment
Security features that keep the driver and vehicle safe and secure should be considered during the vehicle procurement process.
In addition to the risk of vehicles being stolen for use in terrorist attacks, the additional costs to a business caused by the theft of a vehicle and/or load can be considerable.
The decision will depend on what type of operations are being undertaken. A vehicle being used to multi-drop in a town centre might need to be fitted with an ignition immobiliser, while an international haulage operator might need to think about load space monitoring. However, the message is simple: keep the vehicle safe and secure and you reduce not only the costs to your business associated with economic crime, but you also deny a potential terrorist access to a large, heavy vehicle capable of causing great harm when driven deliberately into crowds of people.
The operator must decide what security and safety equipment is most appropriate for their vehicles, from sophisticated electronic engine immobilisers and in-cab cameras to simple steering locks: anything that deters the theft of the vehicle should be considered.
What to do if a vehicle is taken
If your vehicle is stolen call 999 and alert the call handler to the following information:
- circumstances of the vehicle being stolen.
- description of the vehicle including company name, registration details, aerial roof markings and any tracking software fitted in the vehicle.
- if you suspect that the vehicle has been stolen for a terrorist attack then make sure this is made clear to the call handler.
Drivers should also immediately alert the company who will have procedures in place for stolen vehicles.
Disposal of vehicles
Prior to disposal or sale of vehicles to third parties.
All vehicles should have their entire internal and external livery and other markings removed to avoid potential use by others for malicious purposes.
DfT contact details
Please contact DfT’s Land Transport Security Division for further enquiries on goods vehicle security and VAW at: [email protected]
Security tips for goods vehicle drivers
- Avoid talking about loads or routes with unauthorised persons (including over radios and telephones). Do not post information about your route or location on social media, be aware of your ‘digital footprint’, and take care to avoid unwitting disclosure of route/location through mobile phone security settings and geolocation of pictures. Discuss high risk routes with you transport office.
- Lock and secure your vehicle whenever you leave the cab and keep the keys secure, including when unloading and loading, always follow company security policies and instructions.
- Carry out visual walk around checks when leaving and returning to the vehicle to make sure it has not been tampered with. Report any irregularity in loading, locking, sealing or documentation to your Company.
- When conducting walk around checks, think Security as well as Safety.
- Never carry goods for anyone, other than the authorised load.
- If you are forced to change your route, inform your Transport Office immediately.
- If someone is acting suspiciously or something ‘doesn’t feel right’ either at the depot or on the road, report it to ACT, call 0800 789 321 and contact your company.
- Do not allow unauthorised passengers into the cab.
- Keep your phone fully charged and on you at all times. Store important phone numbers.
- Be mindful of your personal security. Keep ID documentation and wallets secure and out of sight.
- Beware of attempts to deceive, such as by bogus Police and DVSA Officers - Stay vigilant always.
Glossary
ACT: Action Counters Terrorism, a national campaign by Counter Terrorism Policing to encourage the public to act on their instincts to help tackle the terrorist threat.
Cab: The cab is an enclosed space in a lorry where the driver is located.
Corporate Social Responsibility (CSR): CSR can help an organisation to show it is socially responsible and environmentally sustainable. To be considered as socially responsible, a company’s activities should benefit society.
CPNI: Centre for the Protection of National Infrastructure, the government authority that provides protective security advice to businesses and organisations across the national infrastructure.
CSAS: Community safety accreditation scheme powers, CSAS is a voluntary scheme under which chief constables can choose to accredit employed people already working in roles that contribute to maintaining and improving community safety with limited but targeted powers.
Operating Centre: A base or depot for Commercial Vehicles
Suspicious Behaviour: Any observed behaviour that could indicate terrorism or terrorism-related crime Transport Office/Operator/Supervisor: Management working in the company offices and are responsible for managing the execution, direction, and coordination of all transportation matters within the organisation.
Summary of sources and further information
| Section | Topic | Organisation |
|---|---|---|
| Section 1: Introduction | CONTEST: The United Kingdom’s Strategy for Countering Terrorism (PDF, 1.4MB) | HM Government |
| Section 2: Security Culture | Security Culture | CPNI |
| Section 2: Security Culture | ACT: Action Counters Terrorism | Counter Terrorism Policing |
| Section 2: Security Culture | Embedding Security Behaviours: using the 5Es | CPNI |
| Section 2: Security Culture | Optimising People in Security | CPNI |
| Section 2: Security Culture | Insider Threat | CPNI |
| Section 2: Security Culture | Personnel Security | CPNI |
| Section 2: Security Culture | Pre-employment Screening | CPNI |
| Section 2: Security Culture | British Standard for Security Screening Employees (BS7858) | BSI |
| Section 2: Security Culture | Pre-Employment Screening: Good Practise Guide | CPNI |
| Section 2: Security Culture | Crowded Places Guidance | NaCTSO |
| Section 3: Site Security | Working with counter terrorism security advisers | NaCTSO |
| Section 3: Site Security | Control Access | CPNI |
| Section 3: Site Security | Lone Working | HSE |
| Section 3: Site Security | Crowded Places Guidance | NaCTSO |
| Section 3: Site Security | CCTV Guidance | CPNI |
Additional sources of information
| Topic | Organisation |
|---|---|
| DfT Rental Vehicle Security Scheme (RVSS) | DfT |
| Dangerous Goods Security Training (PDF, 485KB) | DfT |
| Bus and Coach Security Recommended Best Practice Third edition (PDF, 4.3MB) | DfT |
| Fleet Operator Recognition Scheme | FORS |
| Earned Recognition Scheme | DVSA |
| Professional driving of lorries, buses and coaches | DVSA |
