Cyber security breaches survey 2023: education institutions annex
Published 19 April 2023
Introduction.
This annex includes findings from the samples of UK education institutions included in this year’s Cyber Security Breaches Survey. The results cover:
-
primary schools
-
secondary schools
-
further education colleges
-
higher education institutions.
The annex supplements a main Statistical Release published by the Department for Science, Innovation and Technology (DSIT), covering the this year’s results for businesses and charities.
There is another Technical Annex, available on the same GOV.UK page, that provides the methodological details of the study and copies of the main survey instruments to aid interpretation of the findings.
This research was previously commissioned by the former Department for Digital, Culture, Media and Sport (DCMS). In February 2023, the parts of UK government responsible for cyber security policy moved to the new department, DSIT. Since 2023, the study has also been co-funded and co-developed by the Home Office.
The Cyber Security Breaches Survey is a research study for UK cyber resilience, aligning with the National Cyber Strategy. It is primarily used to inform government policy on cyber security, making the UK cyberspace a secure place to do business. The study explores the policies, processes and approach to cyber security, for businesses, charities and education institutions. It also considers the different cyber attacks and cyber crimes these organisations face, as well as how these organisations are impacted and respond.
For this latest release, the quantitative survey was carried out in winter 2022/23 and the qualitative element in early 2023.
Responsible analyst:
Emma Johns
Responsible statistician
Maddy Ell
Statistical enquiries:
Summary
Prevalence and impact of cyber security breaches and attacks
-
All types of education institutions are more likely to have identified cyber security breaches or attacks in the last 12 months than the average UK business.
-
The proportion of education institutions experiencing breaches and attacks is in line with last year, in contrast to the decline seen for businesses.
-
Further education and higher education institutions are more likely to experience breaches and attacks than schools, and to experience a wider range of attack types, such as impersonation, viruses or other malware, and denial of service attacks.
-
Higher education institutions are more severely affected than schools. Six in ten of the higher education institutions that identified any breaches or attacks report losing money or data, or having compromised accounts used for illicit purposes as a result.
Engagement with cyber security
-
Education institutions typically report a higher level of board engagement with cyber security than the average UK business. In this sense, they are more like large businesses.
-
However, board engagement is sometimes seen as superficial, given the lack of technical expertise on boards and frequent changes in board membership in some institutions.
-
While awareness is growing, there are still many primary and secondary schools that have not heard of government guidance like the National Cyber Security Centre’s (NCSC) 10 Steps to Cyber Security and Board Toolkit, certification schemes like Cyber Essentials, and communications campaigns like Cyber Aware. Awareness of these initiatives is much more widespread in further education colleges and higher education institutions.
Approaches to cyber security
-
Around half of further and higher education institutions have a cyber security strategy in place. This is one of the few areas recorded in the survey where these institutions are behind large businesses (around seven in ten of which have a strategy). However, the qualitative evidence suggests that these institutions have started to move towards more proactive cyber security approaches in recent years.
-
The majority of education institutions have taken action in the last 12 months to help identify cyber security risks (e.g. undertaking risk assessments). Primary schools tend to have less sophisticated cyber risk management approaches than secondary schools, colleges and higher education institutions.
-
All types of education institutions are more likely to have technical controls in place in the five technical areas covered in Cyber Essentials than the average UK business.
Cyber crime
Some cyber security breaches and attacks do not constitute cyber crimes under the Computer Misuse Act 1990 and the Home Office Counting Rules. New questions were added this year to estimate the prevalence of cyber crime in education institutions in the last 12 months, using the principles in the Home Office Counting Rules. As this is the first year these questions have been asked and there is no baseline for comparison, users should be relatively cautious when interpreting these statistics.
-
The prevalence of cyber crime in primary schools is similar to the typical UK business. Around one in ten have experienced any cyber crime in the last 12 months. By comparison, a third of secondary schools have experienced any cyber crime in this time.
-
Cyber crime tends to be more prevalent in further and higher education institutions – around half have experienced any cyber crime in the last 12 months.
-
The survey also estimates fraud that occurs as a result of cyber crime. This is also more prevalent in higher education institutions than in schools, colleges and businesses, with one in ten higher education institutions experiencing these cyber-facilitated frauds.
Chapter 1: Overview of the data
1.1 Summary of methodology
Each year, the Cyber Security Breaches Survey includes two strands – a quantitative survey and follow-up qualitative interviews with some of the organisations taking part in the survey. Education institutions have been included in the study since 2020.
Quantitative survey
Ipsos carried out a random probability survey of education institutions from 27 September 2022 to 18 January 2023. It included:
-
241 primary schools
-
217 secondary schools
-
44 further education colleges
-
52 higher education institutions.
All institutions were offered both a telephone and online survey. The majority of the primary schools (97%) and secondary schools (94%) in the sample took part by phone. By contrast, the majority of sampled colleges (59%) and universities (79%) took part online.
The school samples include a random selection of free schools, academies, Local Authority-maintained schools and special schools.
The samples were selected from the following sources:
-
all institutions in England from the Get Information About Schools database
-
schools in Scotland from the Scottish Government School Contact details
-
further education colleges in Scotland from the Colleges Scotland directory
-
schools in Wales from the Welsh Government Address list of schools
-
further education colleges in Wales from the Welsh Government Further Education Institutions contact details page
-
schools in Northern Ireland from the Northern Ireland Department of Education database
-
further education colleges in Northern Ireland from the NI Direct FE College directory
-
online lists of all UK universities, e.g. the Universities UK website, cross-referenced against the comprehensive list of Recognised Bodies on GOV.UK (which also includes, for example, degree-awarding arts institutes).
In addition, Ipsos created an open link to the online survey to be disseminated by Jisc and UCISA – representative bodies for individuals working in IT and cyber roles in colleges and universities – to their members. In total, 21 colleges and 31 universities took part in the survey via this open link (and these are included in the total completed interviews).
Qualitative interviews
We carried out 15 qualitative interviews with institutions that took part in the survey, including:
-
2 primary schools
-
6 secondary schools
-
7 higher education institutions.
The qualitative findings offer more nuanced insights into the attitudes and behaviours of education institutions with regards to cyber security. The findings reported here represent common themes emerging across multiple interviews. Insights and verbatim quotes from individual institutions are used to illustrate findings that emerged more broadly across interviews. However, as with any qualitative findings, these examples are not intended to be statistically representative.
The main Statistical Release attributes verbatim quotes to interviewees from businesses and charities by their job role and the size of their organisation. For education institutions, we have only attributed quotes by the type of institution (primary school, secondary school or higher education institution). This is to avoid being disclosive. It is also a reflection of the fact that all education institution interviewees were IT or cyber specialists, whereas among businesses and charities there was more variation (including interviews with non-specialist staff who identified themselves as responsible for the organisation’s cyber security).
1.2 New cyber crime estimates
To increase the value of these statistics, the 2023 iteration of the study includes, for the first time, estimates of cyber crime, and fraud that occurred as a result of cyber crime. These estimates are covered in Section 2.8.
As this is the first year these questions have been asked and there is no baseline for comparison, users should be relatively cautious when interpreting these statistics. This includes, for example, considering the findings for education institutions in the context of the wider results for businesses and charities reported in the main Statistical Release, and not in isolation.
The full details of how these estimates have been arrived at are in the Technical Annex.
1.3 A note on survey representativeness
The education institution survey samples are all unweighted. They were surveyed as simple random samples, with no stratification. As such, they should be considered as representative samples. As the sample sizes are relatively small compared to the business and charity survey samples, the margins of error are higher:
-
±4-6 percentage points for primary schools
-
±4-7 percentage points for secondary schools
-
±8-14 percentage points for further education colleges
-
±7-11 percentage points for higher education institutions.
The range reflects the specific survey result being examined. Results closer to 0% or 100% have lower margins of error, while results of 50% have the highest margin of error.
Due to the relatively small overall sample sizes for each group, it is not possible to break down these results by subgroup (e.g. to look at results by geographic location). We have also avoided doing this due to the risk of disclosure (i.e. revealing the institutions that took part in the survey).
1.4 Comparability to the main results for businesses and charities
In this annex, we have primarily compared our four education institution samples from the quantitative survey against each other, and against the benchmarks set by UK businesses. We only comment on statistically significant differences. The findings are intended to give a broad view of where schools, colleges and higher education institutions lie in relation to businesses when it comes to cyber security.
1.5 Comparisons with previous surveys
We compare the findings from 2023 quantitative survey with equivalent findings from the 2022 survey, pointing out where differences are statistically significant. Because of the very small sample sizes for further education colleges (34 in 2022 and 44 in 2023) and higher education institutions (37 in 2022 and 52 in 2023), there are relatively few statistically significant changes over time to speak of for these groups.
Where appropriate, the report also comments on longer-term changes since 2020 (the first year that education institutions were included in the survey). This analysis seeks to identify broad patterns of change over time, rather than specific instances of statistically significant changes.
Chapter 2: Detailed findings
2.1 Prevalence and impact of cyber security breaches or attacks
This section explores the extent, nature and impact of cyber security breaches or attacks on education institutions over the past year. It is important to remember that the survey can only measure the breaches or attacks that organisations have themselves identified. There are likely to be hidden attacks, and others that go unidentified, so the findings reported here may underestimate the full extent of the problem.
As Figure 2.1 shows, all types of education institutions are more likely to identify breaches or attacks than the average UK business. This is different from 2022, when primary schools and UK businesses were more in line with each other. It reflects the fact, explored in depth in the main Statistical Release, that the prevalence of cyber security breaches and attacks has declined among businesses this year (from 39% in 2022, to 32% in 2023), predominantly driven by a fall among micro businesses.
By contrast, the results for all four types of education institutions are not observably different from last year. While the estimates for secondary schools, colleges and higher education institutions are lower than last year, these changes are not statistically significant. The longer-term trend does not suggest any consistent shift upwards or downwards for any of the four groups since 2020 (when education institutions were first included in the survey).
It remains the case that primary schools are the least likely of the four education groups to experience breaches or attacks, whereas further and higher education institutions are, jointly, the most likely. This continues a pattern from previous years, going back to 2020.
Figure 2.1: Percentage of organisations that have identified breaches or attacks in the last 12 months
| Primary schools | 41% |
| Secondary schools | 63% |
| Further education colleges | 82% |
| Higher education institutions | 85% |
| Businesses | 32% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges; 52 higher education institutions; 2,263 UK businesses
Types of breaches or attacks identified
The findings reported in the rest of this section (Section 2.1) are based only on the institutions that have identified any breaches or attacks.
Figure 2.2 breaks down the types of breaches or attacks experienced. It shows a set of results similar to UK businesses in some ways. For example, phishing attacks are by far the most common type of breach or attack identified, followed by online impersonation, then viruses, spyware or malware.
Nevertheless, in other ways the results are very different across the different education institutions, and diverge from the experience of businesses.
-
Further and higher education institutions are more likely to have experienced a wider range of different types of breaches and attacks than the typical school or business. A higher proportion of these institutions identify impersonation, viruses or other malware, denial of service attacks, and breaches or attacks that fall into another category.
-
Higher education institutions specifically are more likely than colleges to experience at least one breach or attack involving impersonation, viruses or malware, unauthorised access by staff, and the “other” category.
-
Secondary schools are more likely than primary schools to identify instances of online impersonation, unauthorised access by students, and unauthorised access by staff.
Figure 2.2: Percentage that identified the following types of breaches or attacks in the last 12 months, among the organisations that have identified any breaches or attacks
| Type of breach or attack | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Phishing attacks | 84% | 86% | 92% | 100% | 79% |
| Others impersonating organisation in emails or online | 23% | 42% | 64% | 86% | 31% |
| Viruses, spyware or malware (excluding ransomware) | 10% | 16% | 31% | 64% | 11% |
| Unauthorised accessing of files or networks by students* | 6% | 15% | 11% | 20% | 0% |
| Hacking or attempted hacking of online bank accounts | 5% | 4% | 3% | 7% | 11% |
| Takeover of organisation’s user accounts | 5% | 7% | 6% | 16% | 9% |
| Ransomware | 5% | 3% | 6% | 9% | 4% |
| Denial of service attacks | 3% | 8% | 44% | 30% | 7% |
| Unauthorised accessing of files or networks by staff | 2% | 12% | 11% | 43% | 2% |
| Unauthorised accessing of files or networks by outsiders | 1% | 1% | 14% | 16% | 2% |
| Unauthorised listening into video conferences or instant messages** | 0% | 1% | 3% | 7% | 0.5% |
| Any other breaches or attacks | 2% | 2% | 17% | 43% | 4% |
Bases (those that identified a breach or attack in the last 12 months): 98 primary schools; 137 secondary schools; 36 further education colleges; 44 higher education institutions; 887 businesses
*This code was not applicable to businesses.
**Values greater than 0% but too small to be rounded up to 1% are shown as 0.5%.
On the whole, these findings are similar to those seen in 2022, although there has been a decline in instances of unauthorised listening into video conferences or instant messages. This has fallen for secondary schools (to 1% in 2023, vs. 9% in 2022) and for higher education institutions (to 7% in 2023, vs. 26% in 2022). This reduction may be due to attempts from schools and universities to return to more in-person working and teaching around two years since the start of the COVID-19 pandemic.
How are education institutions affected?
Among those that have experienced breaches or attacks in the last 12 months, higher education institutions appear to be more severely affected by them than schools. The estimates for colleges are nominally in between the other groups, but the differences between colleges and schools are not statistically significant.
-
Half (50%) of higher education institutions and three in ten further education colleges (31%) reported experiencing breaches or attacks at least weekly. In comparison, primary schools (15%) and secondary schools (20%) are less likely to experience breaches or attacks every week. Schools are much closer to the typical UK businesses identifying breaches or attacks (21% of which experience them weekly).
-
Six in ten higher education institutions (61%) experience a negative outcome, such as a loss of money or data from any breaches or attacks. This compares to 22% of primary schools, 24% of secondary schools and 36% of colleges. Schools are closer to the typical business (24%) in this regard.
-
Almost half (45%) of higher education institutions state that their accounts or systems were compromised and used for illicit purposes – the most common negative outcome they mention in the survey. It is worth noting that this specific outcome is only mentioned by 8% of large businesses, making this a much more substantial problem for universities than for other large organisations. This marked difference was also present in 2022.
-
Three-quarters (75%) of higher education institutions say they were negatively impacted regardless of whether there was a material outcome or not. Most commonly, they report needing additional staff time to deal with the breach or attack, or to inform customers or stakeholders (70%) and new measures being needed to prevent or protect against future breaches or attacks (48%). By contrast, primary schools (37%) and secondary schools (49%) are less likely to report being negatively impacted by breaches or attacks, while this applies to six in ten (61%) further education colleges. Primary schools are in line with the typical business (also 37%), while other institutions are closer to large businesses (52% of which identify a negative outcome).
2.2 Perceived impacts of current geopolitical and economic factors on cyber security
The qualitative interviews with schools and higher education institutions explored how major geopolitical events like the war in Ukraine and state-sponsored cyber attacks may have impacted their approaches to cyber security. The interviews also covered the perceived impact of broad economic factors, such as inflation, rising energy prices and budget concerns.
Geopolitical factors
The main Statistical Release lays out that, among the businesses and charities that did not operate internationally, there tended not to be much focus on whether cyber attacks were state-sponsored or not. Schools were similar in this regard.
There was a sense among some schools that state-sponsored attacks were already commonplace, but that events like the war in Ukraine had heighted awareness of what was already happening. One secondary school interviewee speculated that attacks from countries like Russia may have increased slightly in this context. However, in general, this perception had not influenced schools’ approaches to cyber security.
The school website gets attacked by Russia and China a lot – hundreds of hits a day. That’s gone up a bit.
– Secondary School
The one thing would be, when the Russian-Ukrainian war started, there was a big story about Russian hackers, but I wouldn’t say it was more of an increase in awareness than usual in the long term.
– Secondary School
Higher education institutions tended to say more in interviews about the threats from specific countries, because of their international presence, or research partnerships with other countries. The actions taken by these institutions were driven not only by media stories, but also by guidance from the National Cyber Security Centre (NCSC), and sometimes by pressure from international funders and partners. For example, one higher education institution interviewee had started planning more for the risk of device tampering by foreign states, based on NCSC guidance. Another discussed revisiting relationships with certain countries to remain compliant with US funding streams.
The higher education institutions we spoke to were continuing to monitor the situation around state-sponsored attacks. There was some speculation that this problem may get worse within the next year.
I’m anticipating more attempts to access our research, but it hasn’t happened yet.
– Higher education institution
Importantly, these interviews highlighted that higher education institutions did not necessarily see cyber attacks as their biggest state-related issues. There were other, broader issues emerging from the changing geopolitical situation, such as the threat of intellectual property theft, or foreign students no longer being able to pay fees.
IP theft of research is a concern, rather than a cyber security threat.
– Higher education institution
Economic factors
In contrast to the geopolitical factors, the discussion around economic factors was more substantial in schools. Some interviewees voiced concern about how their organisations would continue to maintain a focus on cyber security in the face of increasing budget pressures. However, much like the findings among businesses and charities, this was typically speculation about what might happen, rather than actions that had already been taken.
The support staff salaries are going up. National Living Wage is going up. We’re going to have to find the money to do that, and that’ll come from all the other budgets. The roof is leaking. The fuel bills are huge. We just can’t even begin to look at cyber security now. Because it’s one of the costliest things, IT is the first to go.
– Primary school
Your biggest income is coming from the number of students you’ve got. With falling pupil numbers the easy thing to cut is IT spend, but it’s got to a point where there isn’t anything left to cut. It’s difficult.
– Secondary school
I think [cyber security] has been seen as an easy thing to cut. I don’t think anybody truly understands enough about it not to just lump it [cyber security] in with the wider IT spending.
– Higher education institution
2.3 Sources of information and guidance
Seeking information
All the higher education institutions (100%) in our survey sample have sought information or guidance about cyber security from external sources in the last 12 months. Nine in ten colleges (92%) have done so. Both these figures suggest greater information seeking from these groups than in 2022 (when it was 78% of higher education institutions and 74% of colleges).
Information seeking is slightly less common an action in primary schools (71%) and secondary schools (74%), compared to these larger institutions. Nevertheless, it is worth noting that schools are more in line with medium businesses (at 72%) than the typical UK business (49%).
We ask where institutions have sought information or guidance. To note, this is unprompted for those doing the survey by telephone, while those doing it online look at a prompted response list. The online list tends to generate a wider range of answers, so there should be caution when comparing the specific information sources mentioned by schools (most of which took part by phone) with those mentioned by colleges and universities (which mainly took part online).
The most common sources of information and guidance, across all institutions, are:
-
any government or public sector sources (for 70% of higher education institutions, 55% of further education colleges, 34% of secondary schools and 35% of primary schools)
-
external cyber security or IT providers (for 54% of higher education institutions, 16% of further education colleges, and 30% of both primary and secondary schools).
To note, Jisc is mentioned by 74% further education institutions and 84% of higher education institutions. Jisc is a not-for-profit company that provides digital infrastructure, services, and guidance specifically for these organisations. This has been an influential source in previous years as well, although this year’s especially high scores should be considered in the context of the methodological changes. This year, Jisc promoted the open link online survey directly to its members for the first time. As such, any increase in organisations mentioning Jisc may not be true changes over time.
There are also important differences in the results between the various types of institutions:
-
Schools are more likely to have reached out to local authorities (13% of primary schools and 6% of secondary schools have done so, whereas no further or higher education institutions in our sample mention local authorities). This may reflect that certain state schools are funded and managed by local authorities.
-
By contrast, within colleges and higher education institutions, the most prevalent public sector information sources are the NCSC (used by 42% and 70% respectively). Just 4% of primary schools and 13% of secondary schools mention this government organisation.
-
Higher education institutions (54%) are more likely than colleges (16%) to have looked to external cyber security or IT providers.
Qualitative insights on information sharing and reliance on partners
In the qualitative interviews, higher education institutions in particular highlighted a culture of sharing information and learning with each other, with networks like the Jisc cyber security community group facilitating this sort of support and guidance. This sort of culture was less present in private sector businesses in the qualitative strand.
As a university, we get a lot out of Jisc. They offer a lot of help and guidance. Unlike the private sector, our competitors will share information on IT security issues … There is lots of support from other peer institutions.
– Higher education institution
It’s difficult for non-technical people to understand the potential damage of an attack or ransomware incident. Sharing learnings has helped to give the ‘human angle’, the effort involved in recovery.
– Higher education institution
Schools, on the other hand, sometimes noted a reliance on local authorities for providing their IT services, as well as support and guidance on cyber security. Therefore, if relationships with the local authority were poor, this negatively impacted cyber security, as this quote from a secondary school suggests:
There is little support from the local authority, as the Head of the school prefers it that way. We do not have a very good relationship with them (the local authority).
– Secondary school
Awareness of government guidance, initiatives and communications (prompted questions)
There are still many primary and secondary schools that have not heard of the various government guidance, initiatives and communications campaigns on cyber security. Awareness of the following government sources (in Figure 2.3) is much more widespread in further education colleges and higher education institutions. The sources covered here include:
-
the national Cyber Aware communications campaign, which offers tips and advice to protect individuals and organisations against cyber crime
-
the 10 Steps to Cyber Security guidance, which aims to summarise what organisations should do to protect themselves
-
the government-endorsed Cyber Essentials scheme, which enables organisations to be certified independently for having met a good-practice standard in cyber security
-
the NCSC’s Board Toolkit, which helps management boards to understand their obligations, and to discuss cyber security with the technical experts in their organisation.
To note, these estimates are based on prompted questions, whereas those from earlier in the section (on all information sources) are from a question that was unprompted for part of the sample.
Figure 2.3: Percentage of organisations aware of the following government guidance, initiatives, or communication campaigns
| Government guidance, initiative, or communication campaign | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Cyber Aware campaign | 55% | 54% | 61% | 76% | 27% |
| 10 Steps to Cyber Security guidance | 38% | 42% | 68% | 87% | 14% |
| Board Toolkit* | 27% | 27% | 53% | 82% | 22% |
| Cyber Essentials scheme | 17% | 51% | 95% | 100% | 14% |
Bases: 229 primary schools; 212 secondary schools; 38 further education colleges; 38 higher education institutions; 1,152 UK businesses (255 medium or large businesses asked about the Board Toolkit)
*For the business survey, this question was only asked of medium and large businesses rather than the full sample.
Schools’ awareness of the Cyber Aware campaign has increased over time, as Figure 2.4 shows. For primary and secondary schools, current levels of awareness are higher than in 2020, when the survey of education institutions started. However, for colleges (which were not included in the 2020 reporting), awareness has moved in the other direction. As a point of comparison, awareness of Cyber Aware has fallen among all UK businesses since 2021 as well (from 34% to 27%).
Figure 2.4 does not include further or higher education institutions, as the shifts over years in this sample are not statistically significant. For instance, 56% of further education colleges recalled the Cyber Aware campaign in 2021.
Figure 2.4: Percentage of schools over time aware of the government’s Cyber Aware communications campaign
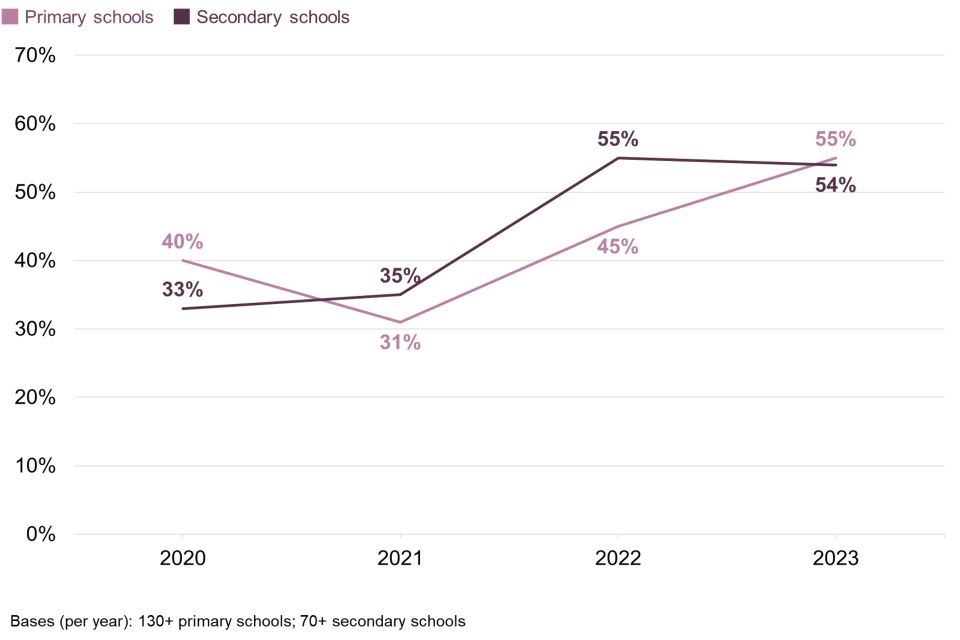
On the other government sources covered in Figure 2.3 (the 10 Steps, Board Toolkit and Cyber Essentials), there are no significant changes from 2022. Nevertheless, the long-term trend shows that awareness of these three sources continues to be higher than before, when these questions were first asked, among secondary schools:
-
Secondary schools’ awareness of the 10 Steps is 13 percentage points higher than in 2020 (when it was 29%).
-
Their awareness of Cyber Essentials is 12 points higher than in 2020 (when it was 39%).
-
Their awareness of the Board Toolkit is 10 points higher than in 2021 (when it was 17%).
By contrast, the long-term trend among primary schools shows no change.
The low sample sizes for higher education institutions each year means we are unlikely to find any statistically significant trend for this group. However, the qualitative interviews reveal that Cyber Essentials (and Cyber Essentials Plus) accreditation was particularly important for higher education institutions, as it was reported as being a more regular requirement when applying for research funding and partnerships.
Increasingly, we’re seeing organisations that want to collaborate with us requiring [us to have] Cyber Essentials Plus. Also, funding for research projects is contingent on these standards and accreditations.
– Higher education institution
2.4 Senior management engagement with cyber security
Quantitative findings on cyber security prioritisation and senior management responsibilities
Education institutions typically report a higher level of senior engagement with cyber security than the average UK business. In this sense, they are more like large businesses. This was also the case in previous years.
-
Almost all say that cyber security is a high priority for their governors or senior management (97% of primary schools, 95% of secondary schools, 95% of colleges and 100% of the higher education institutions we interviewed). These findings are similar to those seen in the 2022 survey, and have remained very consistent over time since 2020. This is in contrast to businesses and charities, which show an apparent fall in prioritisation from last year – a fall driven by the smaller organisations in each group, as discussed in the main Statistical Release.
-
Nine in ten higher education institutions (88%) and three-quarters of colleges (77%) update their governors or senior management on cyber security at least quarterly. This question only has complete data for these two groups this year, meaning the results for schools cannot be reported.
-
Around six in ten schools have a governor or senior manager with responsibility for cyber security (63% of primary schools and 61% of secondary schools, vs. 30% of businesses and 53% of large businesses). Seven in ten further education colleges (70%) and almost nine in ten higher education institutions (87%) similarly assign this responsibility at this senior level.
Qualitative insights on senior management engagement
Similar to businesses and charities, the qualitative interviewees in education institutions highly valued engagement from their board members on cyber security. They felt it gave cyber security a voice at a senior level, showed wider staff that cyber security was a priority, and helped to embed cyber security within broader risk management processes.
We have good, solid support at the Executive Board level … We have interest from the board, and they pay attention when we talk to them.
– Higher education institution
The drivers of board engagement in cyber security in education institutions also matched those in businesses and charities. We heard examples of board members that had a prior interest in the topic area (e.g. a headteacher with an IT degree), auditors recommending that board members have greater oversight of cyber security, and board members starting to ask more questions after seeing government guidance. One higher education institution interviewee had provided their board with material based on the NCSC’s Board Toolkit, and had since then set up monthly meetings with their Head of Business Continuity, marking the start of a more direct working relationship with their board.
Other interviewees noted the importance of government directives in this space. They suggested that the boards in their institutions were so time poor or uninterested, that they would only engage with a topic like cyber security if compelled to do so by the government.
As much as we at the coal face want to try to make these cyber security improvements happen, unless you get senior buy-in … we need the government to tell them.
– Higher education institution
More regular updating of policies is the best form of action. The best way to get help for that is from the government, as people adhere specifically to what they publish. People don’t then go further, so having more guidance would keep everything more secure in general.
– Secondary school
In previous years, the General Data Protection Regulation (GDPR) has been raised as another factor driving board engagement with cyber security. This appears to have softened this year. Education institutions still felt it was important to adhere to data protection regulations, and to take associated cyber security measures. However, there was a sense in some institutions that, now data protection policies and procedures were fully in place, the board no longer needed to get involved. One secondary school interviewee suggested that the attitude of their senior leadership team towards cyber security had regressed since 2018, when GDPR was implemented, in the face of mounting new priorities.
I don’t think it’s even on the senior leadership team’s radar at the moment. We’ve gone through a curriculum redesign, and we’re moving into a new building, so cyber security gets left.
– Secondary school
There were also several concerns raised in interviews about the superficiality of current board engagement in cyber security, where the policies and structures in place did not necessarily match actions. In some cases, interviewees felt their boards considered cyber risks to be below other major institutional risks.
I don’t think anybody particularly realises it’s as big a risk as it is, when virtually every piece of data now is stored on the computer. To us in the IT department, it is important, but in the wider strategy it is probably low down on the priority list. Until something happens. Then it’s right at the top.
– Secondary school
One higher education institution interviewee noted that their board had a manual for how to deal with major physical incidents like fires, floods, bomb threats and pandemics, but this did not cover cyber incidents. Another interviewee from a higher education institution described how the advice of their long-established cyber incident response team tended not to be acted on by the board. Several interviewees reported that – just as in some of the smaller businesses interviewed – their institution’s board members felt that cyber security was safe in the hands of external contractors, resulting in them (the board) disengaging from the topic and understanding the actions being taken, both internally and externally.
I attend governor meetings and cyber security doesn’t come up. Not even under ‘any other business’. Possibly because we have confidence in our external helpdesk.
– Secondary school
There was also a sense across interviews that boards frequently conflated cyber security with other topics, such as GDPR, compliance with regulations more generally, and online safeguarding issues. For instance, we spoke to one secondary school where online safeguarding was a top priority, and cyber security was mostly focused on monitoring students’ internet usage and discussing safeguarding issues in computer science lessons.
Various reasons were given to explain this relatively superficial engagement with cyber security, and the idea that it was considered a second-tier priority, or simply treated as part of a bigger priority issue. Interviewees frequently remarked that their boards were made up of teachers or academics, who were not capable of being technical cyber security experts, and had little time to engage more deeply. Alongside this, one interviewee highlighted that cyber security was developing all the time, making it challenging for board members to keep up. One higher education institution interviewee also noted that their board membership changed regularly, making it challenging to instil a sense of importance over time, and to maintain the same level of awareness and training across all board members.
There were some examples of how institutions had attempted to overcome these constraints (around board expertise, time and capability). One secondary school with academy status had cyber security managed by the academy group (which covered several schools), rather than the board of governors. This meant the interviewee, in charge of cyber security within their school, had a direct line of communication with an engaged Chief Operating Officer and Chief Finance Officer, bypassing the board of governors. Others highlighted how they had provided specialised awareness-raising sessions tailored to the board, which in some cases involved bringing in an external expert to talk to them. One interviewee from a higher education institution explained the importance of showing board members the risks for end users, such as intellectual property theft and the impact on the student experience.
Student experience, that is the fundamental thing for us. It will be bad for them if we get breached. Value for money is also a key driver.
– Higher education institution
2.5 Identifying cyber security risks
Actions taken to identify risks
The majority of the education institutions have taken at least one of the actions shown in Figure 2.5 in the last 12 months, to help identify cyber security risks. Primary schools tend to have less sophisticated approaches, whereas secondary schools, further education colleges and higher education institutions tend to have more sophisticated approaches. All types of education institutions are more likely than the typical UK business to have taken the various actions.
Further education colleges and higher education institutions are specifically more likely than schools to be carrying out vulnerability audits and penetration testing, and to be investing in threat intelligence.
Figure 2.5: Percentage of organisations that have carried out the following activities to identify cyber security risks in the last 12 months
| Activities to identify cyber security risks in the last 12 months | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Any of the listed activities | 74% | 89% | 98% | 100% | 51% |
| Risk assessment covering cyber security risks | 48% | 57% | 66% | 87% | 29% |
| Used specific tools designed for security monitoring | 41% | 61% | 70% | 85% | 30% |
| Testing staff awareness and response (e.g. mock phishing) | 43% | 56% | 75% | 62% | 19% |
| A cyber security vulnerability audit | 27% | 40% | 59% | 85% | 15% |
| Penetration testing | 19% | 34% | 68% | 88% | 11% |
| Invested in threat intelligence | 13% | 26% | 57% | 71% | 9% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges;
52 higher education institutions; 2,263 UK businesses
Over the last three years, an increasing proportion of primary schools have said they have carried out penetration testing (19% in 2023, vs. 12% in 2022 and 9% in 2021).
Secondary schools are less likely to have invested in threat intelligence this year (26%, vs. 37% in 2022). This may have been an atypically high result last year, since it was 23% in 2021 and 22% in 2020.
There has also been a fall in the proportion of higher education institutions that have invested in threat intelligence this year (71%, vs. 89% in 2022).
Reviewing supplier risks
All types of education institutions are more likely than businesses to say they have reviewed supplier-related risks to cyber security, as Figure 2.6 shows. Nevertheless, just as with businesses, it is more common to review immediate suppliers than the wider supply chain. This is also one of the few areas of the survey where a relatively large proportion – in this case half – of higher education institutions have not taken action.
Figure 2.6: Percentage of organisations that have carried out work to formally review the potential cyber security risks presented by the following groups of suppliers
| Groups of suppliers | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Their immediate suppliers | 28% | 33% | 32% | 50% | 13% |
| Their wider supply chain | 18% | 18% | 18% | 23% | 8% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges;
52 higher education institutions; 2,263 UK businesses
Qualitative insights on cyber security risks linked to supply chains
The education institutions we spoke to in the qualitative interviews typically had more stringent supply chain cyber risk management processes than businesses and charities. Examples included:
-
use of approved supplier frameworks (e.g. Jisc frameworks)
-
use of software to support supplier compliance checks (e.g. GDPR in Schools software, that helps schools undertake data protection impact assessments with suppliers)
-
demanding information on third-party suppliers’ IT and cloud systems during procurement
-
demanding accreditations (e.g. ISO 27001 or Cyber Essentials)
-
undertaking risk assessments where suppliers would have access to IT systems
-
restricting supply teachers (in schools) to guest Wi-Fi networks.
Nevertheless, there was still a sense from interviewees that that supply chain cyber risk management could be improved. One primary school interviewee said they would welcome more support from the Department for Education or NCSC to find approved or certified suppliers for schools.
Schools and higher education institutions both noted various challenges around supply chain cyber risk management. The sheer number of third-party suppliers was a significant challenge for higher education institutions. One also pointed out that aspects of procurement were managed both centrally and within departments, creating tiered supply chain systems.
There’s no way we know everything that suppliers are doing. There are hundreds of third-party services in use.
– Higher education institution
One similarity with the business and charity findings was a sense that there was a greater focus on IT and technology providers in education institutions, for example with dedicated IT procurement teams. However, some interviewees felt this meant cyber risks from other physical suppliers were sometimes overlooked and could be exploited.
We are weaker on things not IT – for example if someone bought an internet-connected fridge and it turns out it comes from China
– Higher education institution
One university had, in the last year, experienced a cyber incident emanating from an accounting supplier listed on the NHS supply chain database. The supplier was contracted to scan expense receipts. They were compromised in a ransomware attack that led to data being lost. In this case, the interviewee considered themselves lucky, as the university had only been using the local network version of the software, and not started using the cloud version (which may have led to a far more substantial breach).
Another challenge specific to higher education institutions was around partnership working between individual academics across institutions. One interviewee highlighted, as an example, that their academic staff might be asked by researchers at other institutions to use Dropbox to host documents, rather than their own university’s approved cloud provider, Microsoft. These situations made managing supplier risks difficult without stifling academic collaboration, as staff could not put university files or data on Dropbox under their own rules.
2.6 Actions taken to manage or mitigate risks
Cyber security strategies (quantitative and qualitative findings)
Around half of further education colleges (50%) and higher education institutions (52%) have a formal cyber security strategy in place. This compares to 68% of large businesses – this is one of the few areas recorded in the survey where colleges and universities are behind large businesses. These results are not significantly different from last year.
The findings cannot be reported for schools due to sample limitations.
The qualitative findings suggest that many education institutions have just started to pull together formal cyber security strategies in the past two years. As such, several strategies had not matured yet, and interviewees had not evaluated their success. However, multiple interviewees said that their approaches to cyber security had become more proactive than before. Specific examples, mainly from higher education institutions, of more proactive approaches included assigning formal responsibility for cyber security to board members, giving cyber security operational independence from traditional IT departments, and giving it a separate budget. One institution had moved from yearly budgeting to ad hoc budgeting for cyber security, which they felt was superior, as it allowed them to better adapt to constant changes in exchange rates and to emerging tech solutions.
As with businesses and charities, there were various factors that had led to the development of formal cyber security strategies, including:
-
reviews of approaches in various areas emerging from the COVID-19 pandemic
-
reactions to NCSC guidance (e.g. to the 10 Steps)
-
requirements from other public sector funders or partners of higher education institutions (e.g. the NHS).
In interviews with schools, compared to higher education institutions, it was more typical for cyber security and IT to be considered synonymously, and for cyber security spending to be part of overall IT budgets. In these environments, interviewees highlighted the importance of making persuasive business cases to management boards for spending – as was the case with small and medium businesses.
The only way to secure budget is to outline the worst-case scenario. You’ve got the personal data of 600 children, staff bank accounts and addresses, medical records, you can lose access to your entire network and not be able to teach.
– Secondary school
Another challenge facing schools was around restructuring. We spoke to two schools that had both had to put cyber security investment and planning decisions on hold, ahead of being integrated into a new academy structure.
We’re in a bit of a state of flux with everything. We haven’t really got an IT strategy at the moment. The Trust is new, so there’s no strategy for overarching IT for every school yet. I think probably something may be coming, to say what they want everybody to do.
– Secondary school
Insurance against cyber security breaches
Half of primary schools (50%) and just under half of secondary schools (46%) report being insured against cyber risks. For both sets of schools, this is mainly worked into a broader insurance policy (in 39% of primary schools and 33% of secondary schools). As Figure 2.7 shows, insurance has become an increasing feature of schools’ approaches to cyber security over the last four years.
Figure 2.7: Percentage of schools that have any type of insurance against cyber security risks
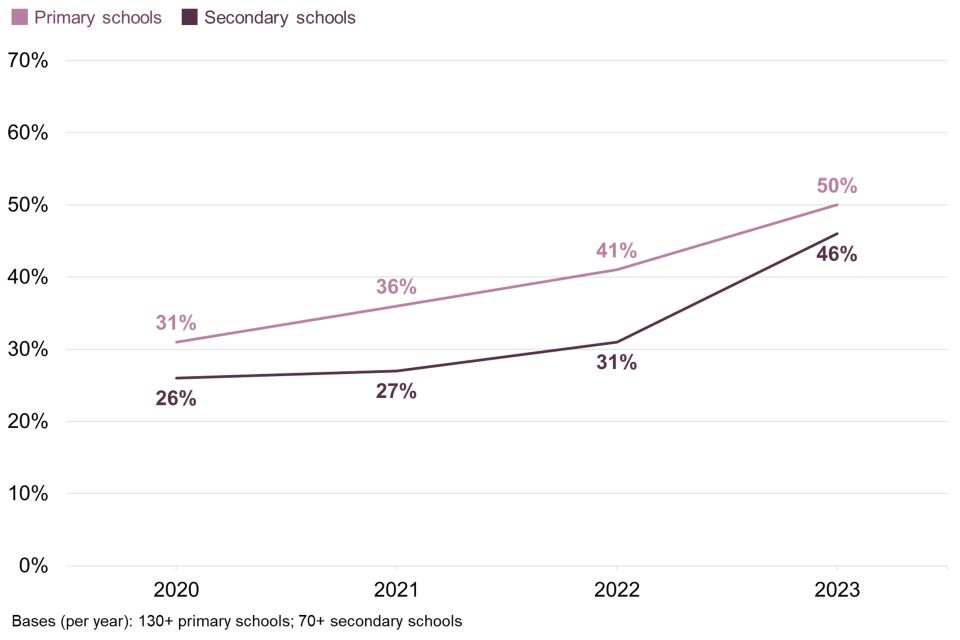
Nonetheless, it is worth noting that almost half of the individuals in cyber roles that we interviewed in primary and secondary schools did not know whether their school had this kind of insurance (40% and 38% respectively), despite interviews being undertaken with the individual identified as taking most responsibility for cyber security within the school. This compares to 20% of all UK businesses not knowing. It highlights that cyber security is perhaps more siloed in schools, and still sometimes separately from financial matters like insurance.
This statistic cannot be reported for colleges due to small sample sizes for this question. For higher education institutions, use of cyber insurance is much more commonplace. Seven in ten (70%) have some form of insurance, and over two-fifths (45%) have a specific cyber security insurance policy (as opposed to a more general policy incorporating cyber). This has not changed significantly over time.
With that said, there was a voice of concern raised about cyber insurance for higher education institutions in the qualitative interviews. One higher education institution interviewee reported that, in their experience, many academic institutions were starting to be refused cyber insurance, on the basis that they were not compliant with Cyber Essentials across their student base, or among staff working from home. This may be an area for further investigation in subsequent years.
Technical rules and controls
The survey covers a range of technical rules and controls that organisations may have in place to help minimise the risk of cyber security breaches (split out in Figures 2.8 and 2.9). Many of these are basic good practice controls taken from government guidance such as the 10 Steps to Cyber Security, as well as the guidance associated with the Cyber Essentials scheme.
The government-endorsed Cyber Essentials scheme enables organisations to be independently certified for having met a good-practice standard in cyber security. Specifically, it requires them to enact basic technical controls across five areas:
-
boundary firewalls and internet gateways
-
secure configurations
-
user access controls
-
malware protection
-
patch management (i.e., applying software updates).
All types of education institutions are more likely to have technical controls in place in these five areas than the average UK business. Of the five areas, patch management is the only one that is not covered by around nine in ten or more education institutions, as Figure 2.8 shows. Primary schools are notably weaker in this area, with less than half (46%) having a policy to apply software updates within 14 days.
Figure 2.8: Percentage of organisations that have the rules or controls in place in the five technical areas from Cyber Essentials
| Technical area from Cyber Essentials | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
|
Restricting IT admin and access rights to specific users (user access controls) |
95% | 97% | 98% | 94% | 67% |
| Up-to-date malware protection | 90% | 95% | 98% | 96% | 76% |
|
Firewalls that cover the entire IT network, as well as individual devices (boundary firewalls and internet gateways) |
90% | 94% | 98% | 92% | 66% |
|
Security controls on organisation-owned devices (e.g. laptops) (security controls) |
88% | 92% | 93% | 94% | 59% |
|
A policy to apply software updates within 14 days (patch management) |
46% | 60% | 89% | 67% | 31% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges; 52 higher education institutions; 2,263 UK businesses
Bold wording used in questionnaire
Across all groups of education institutions, there have been no significant shifts in adherence to these Cyber Essentials areas since 2022 or 2021.
The survey also covers a wider range of technical rules and controls, shown in Figure 2.9. The chart raises various differences between education institutions, which have all been seen in previous years:
-
Cloud back-ups are more common than other means of backing up data in primary schools. By contrast, colleges are more likely to use other means for secure back-ups than to use cloud back-ups.
-
Schools continue to be more likely than colleges and higher education institutions to restrict access to their own devices.
-
Two-factor authentication is more common in further and higher education institutions than in schools.
-
Primary schools are less likely than all the other types of education institutions to have separate Wi-Fi networks for staff and visitors.
Figure 2.9: Percentage of organisations that have additional rules or controls in place (beyond the Cyber Essentials technical areas)
| Rules or controls in place (beyond the Cyber Essentials technical areas) | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Rules for storing and moving personal data securely | 87% | 86% | 68% | 60% | 45% |
| Backing up data securely via a cloud service | 86% | 76% | 59% | 69% | 70% |
| A password policy that ensures that users set strong passwords | 84% | 91% | 95% | 98% | 70% |
| An agreed process for staff to follow with fraudulent emails or websites | 83% | 90% | 75% | 90% | 48% |
| Monitoring of user activity | 73% | 92% | 82% | 87% | 32% |
| Only allowing access via organisation-owned devices | 68% | 56% | 30% | 19% | 55% |
| Any Two-Factor Authentication (2FA) for networks/applications | 63% | 66% | 86% | 98% | 37% |
| A virtual private network, or VPN, for staff connecting remotely | 61% | 64% | 77% | 96% | 31% |
| Backing up data securely via other means | 54% | 82% | 86% | 73% | 45% |
| Separate Wi-Fi networks for staff and visitors | 51% | 87% | 89% | 77% | 34% |
Bases: 2,263 UK businesses, 1,174 charities
In the main Statistical Release, we highlight that the deployment of several technical rules and controls has fallen among micro and small businesses. In other words, there has been a reduction in cyber hygiene measures in this part of the business population. A similar pattern can be observed among primary schools. Specifically, primary schools are now less likely to have in place:
-
a password policy (84%, vs. 94% in 2022)
-
an agreed process around phishing (83%, vs. 90% in 2022)
-
rules for storing and moving personal data securely (87%, vs. 93% in 2022)
-
a VPN for staff connecting remotely (61%, vs. 73% in 2022).
Over the longer-term, since 2020, there has been a consistent fall in the proportion of primary schools that only allow access via their own devices, from 84% in 2020, to 79% in 2021, 74% in 2022 and 68% now. This also mirrors a trend in the business population. It may reflect shifts in ways of working since the COVID-19 pandemic (with the 2021 survey being the first to take place since the start of the pandemic).
Separately, higher education institutions are now less likely than in 2022 to have separate Wi-Fi networks for staff and visitors (77%, vs. 92% in 2022) and to use ways other than the cloud to back up their data (73%, vs. 89% in 2022).
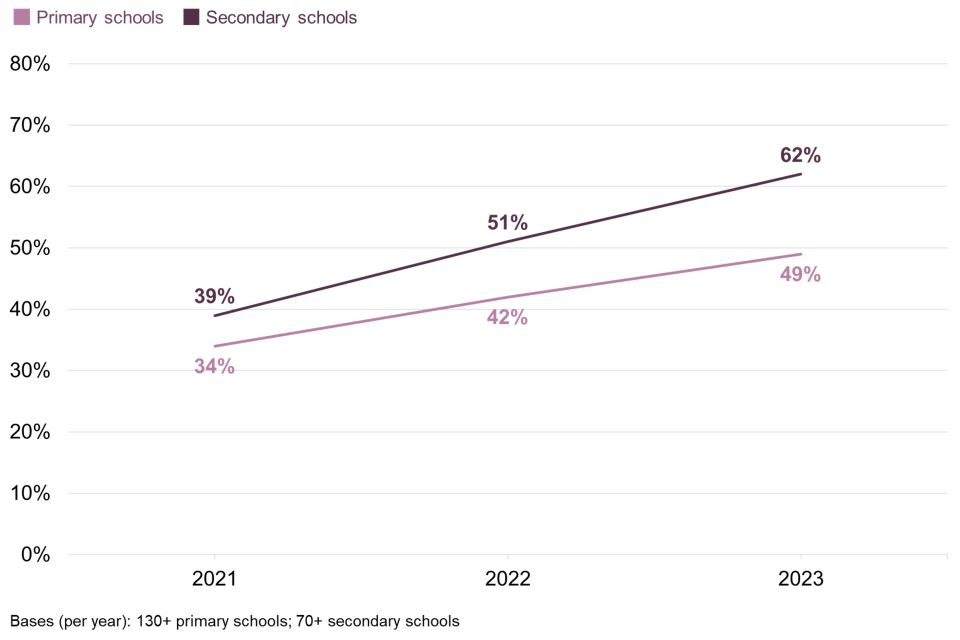
Staff training and awareness raising
Cyber security training or awareness raising activities are less common in schools than further and higher education institutions. Around half of primary schools (49%) and six in ten secondary schools (62%) have undertaken any such activities in the last 12 months. This rises to more than eight in ten further education colleges (86%) and higher education institutions (88%). By comparison, only a fifth of all UK businesses (18%) have carried out such activities.
The three-year trend (which is only available for schools) shows that training and awareness raising activities on this topic have become more common in both primary and secondary schools. This is illustrated in Figure 2.10.
Figure 2.10: Percentage of organisations over time that have had training or awareness raising sessions on cyber security in the previous 12 months
Qualitative insights on cyber security training in education institutions
Various interviewees in the qualitative research highlighted the importance of cyber security training and awareness raising work among wider staff in education institutions.
The ongoing focus is on the people and the training. Those are areas where we can have a big impact, rather than just putting money into the technology and systems.
– Higher education institutions
Many of the barriers and challenges around training and awareness raising were similar to those in businesses and charities, including:
-
staff not having enough time to attend training
-
a lack of resources to run more training
-
a lack of communication between IT and other departments.
Some of the challenges were, however, more unique to certain education institutions than to other organisations. Examples included:
-
a lack of willingness among academic staff in universities to undertake training in general, even when it is labelled as mandatory
-
cyber security training in schools being commonly framed in terms of GDPR, with the latter portrayed as the priority area rather than cyber security itself
-
difficulty in running realistic cyber incident simulations within term time, because of disruption to student learning.
Several education institutions said they thought the most successful training courses were short ones (around 10 to 20 minutes) that could be run frequently and followed up with a discussion. One university was also revamping their training offer to be more tailored to specific staff roles, so that staff would only need to attend the sessions that were relevant for them.
We’re trying to expand our offer to be more relevant to specific roles, so that people want to do it, rather than being forced to. No one says it’s not important, they just don’t have the time.
– Higher education institutions
Another secondary school mentioned tying in staff communications with calendar events like Safer Internet Day, to help raise the profile of cyber security.
Some interviewees mentioned making use of NCSC resources such as the previously mentioned Board Toolkit and free training for school staff. There was also one mention of National Online Safety training. One school did, however, suggest that they felt the NCSC schools training was in need of a refresh, given developments in cyber security since 2021.
Finally, it is worth noting that some institutions were taking opposing approaches to change staff behaviour. Some schools and universities emphasised the importance of good communication and building relationships with staff, to actively move away from a blame culture around cyber incidents – the idea of two-way feedback between those in charge of cyber security and wider staff also came out of the business and charity interviews.
I try and build relationships when I have to attend to one of their issues, and I talk and explain what I’m doing, if I think it’s something that’s simple enough to remember, or might be a recurring problem.
– Secondary school
We sit down with people [after an incident] and talk through the situation, and try to think about how we can stop it happening again. We make sure that that is a key part of the process, always learning and reflecting. Talking in a large group, trying not to focus on blame.
– Higher education institutions
By contrast, it was clear that not all cyber security leads were on board with this approach. One interviewee from a secondary school said that they were focused on making staff compliant by highlighting the negative consequences for them as individuals if something were to go wrong.
The biggest thing that works is fear. This is where, with GDPR, we have to document every mistake and emphasise the problem of fines if we do something wrong, which makes staff a bit more on the ball. This could lead to the threat of getting fired if it’s your fault.
– Secondary school
Outsourcing cyber security
Our sample suggests that outsourcing of cyber security is more common among primary schools than other education institutions. Three-quarters (75%) of primary schools say an external provider manages their cyber security for them, compared with 44% of secondary schools, 14% of further education colleges and 15% of higher education institutions. This follows a similar pattern to previous years, with no significant changes this year.
As previously discussed in Section 2.4, the qualitative findings indicated the great deal of trust that primary and secondary schools placed in external IT providers to manage their cyber security. There was a sense in some interviews that this had led to the senior leadership within the school assuming the issue was dealt with, and disengaging from the topic and the actions being taken, both internally and externally.
Cyber security planning and documentation (including incident response)
In terms of documentation, all four groups of education institutions are far more developed than the typical UK business, and much closer to large businesses. Figure 2.11 shows that cyber security policies and business continuity plans covering cyber security are more common than incident response plans. For example, just half of primary schools have an incident response plan (49%), while two-thirds have cyber security policies (66%).
Figure 2.11: Percentage of organisations that have the following kinds of documentation
| Type of documentation | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| A formal policy or policies covering cyber risks | 66% | 72% | 77% | 90% | 29% |
| A business continuity plan that covers cyber security | 62% | 62% | 80% | 85% | 27% |
| A formal incident response plan | 49% | 55% | 61% | 77% | 21% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges;
52 higher education institutions; 2,263 UK businesses
These figures have not notably changed since 2022.
Figure 2.12 shows the actions that education institutions say they take, or would take, in response to a cyber incident – this is a prompted list. To note, the result for informing insurance providers is specifically taken from the subgroup of education institutions that have any form of cyber insurance (covered earlier in Section 2.6). As such, the sample sizes are too small to report this result for further and higher education institutions specifically.
While higher education institutions and, to a lesser extent, colleges, rate lower than schools on several of these actions, this is likely to reflect how this year’s survey was administered – a relatively large number of further and higher education institutions took part online, where they were explicitly shown the option to say “it depends on the severity of the incident”. Consequently, relatively high proportions have picked this option. For example, 48% of higher education institutions say that informing regulators would depend on the severity of the incident.
Nevertheless, this set of findings demonstrates that higher education institutions are taking an overall more sophisticated approach. It may be that, since the prevalence of breaches and attacks is highest among this group, they cannot take a uniform approach to every incident and have to make more case-by-case judgements.
Figure 2.12: Percentage of organisations that say they take, or would take, the following actions following a cyber security incident
| Actions that organisations take, or would take, following a cyber security incident | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Keep an internal record of incidents | 87% | 90% | 91% | 87% | 62% |
| Formal debriefs or discussions to log any lessons learnt | 86% | 83% | 73% | 63% | 59% |
| Inform your directors or trustees of the incident | 85% | 83% | 68% | 44% | 80% |
| Inform your cyber insurance provider (among those with insurance)* | 83% | 84% | 0% | 0% | 69% |
| Assess the scale and impact of the incident | 82% | 87% | 86% | 85% | 62% |
| Inform a regulator of the incident when required | 87% | 84% | 73% | 50% | 57% |
| Attempting to identify the source of the incident | 58% | 81% | 84% | 69% | 57% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges;
52 higher education institutions; 2,263 UK businesses
*Sample sizes are under 30 for this code for further and higher education institutions.
At the start of this subsection, we note that formal incident response plans are a less common aspect of cyber security documentation in education institutions (relative to policies and business continuity plans). Figure 2.13 shows the other kinds of documentation, guidance and processes that organisations have in place for such incidents – again, this is a prompted list in the survey.
The findings in Figure 2.13 highlight that, as with businesses, while a large majority of schools and colleges say (in the preceding Figure 2.12) that they will take several actions following a cyber incident, fewer have agreed processes already in place to support this.
Here, higher education institutions are more likely than others to have plans that encompass assigning roles and responsibilities to specific individuals, as well as communications and public engagement plans. Nevertheless, the results indicate that around a third of higher education institutions do not have public engagement plans in place.
Figure 2.13: Percentage of organisations that have the following measures in place for dealing with cyber security incidents
| Measures for dealing with cyber security incidents | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Roles or responsibilities assigned to individuals during or after incident | 66% | 70% | 73% | 92% | 36% |
| Guidance for when to report externally (e.g. to regulators or insurers) | 62% | 62% | 68% | 71% | 26% |
| Written guidance on who to notify | 60% | 72% | 66% | 79% | 26% |
| External communications and public engagement plans | 38% | 41% | 41% | 67% | 13% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges;
52 higher education institutions; 2,263 UK businesses
Trends over time in incident response
Compared with 2022, schools are now less likely to have taken various actions or have measures in place; specifically:
-
Primary schools are less likely to say they would inform directors, trustees or governors of the incident (85% in 2023, vs. 96% in 2022), make an assessment of the scale and impact of the incident (82% vs. 89%), and to attempt to identify the source of the incident (58% vs. 68%). They are also less likely this year to have written guidance in place on who to notify in the event of a cyber incident (60% vs. 75%).
-
Secondary schools are also less likely to inform directors, trustees or governors of the incident (83% in 2023 vs. 95% in 2022), attempt to identify the source of the incident (81% vs. 91%). Like primary schools, they are also less likely this year to have guidance on when to report incidents externally (62% vs. 74%).
We have not reported changes over time at this question for further and higher education institutions, because of the influence of the online survey mode on responses to this question in particular. The results for schools are not affected by this, as very few schools took part online. More details can be found in the Technical Annex.
2.7 Implementing the 10 Steps to Cyber Security
The government’s 10 Steps to Cyber Security guidance sets out a comprehensive risk management regime that organisations can follow to improve their cyber security standards. It is not, however, an expectation that organisations comprehensively apply all the 10 Steps – this will depend on each organisation’s cyber risk profile.
These steps have been mapped to several specific questions in the survey (in Table 2.1), bringing together findings that have been individually covered across the rest of this chapter. This is not a perfect mapping – some of the Steps are overlapping and require organisations to undertake action in the same areas – but it gives an indication of whether organisations have taken relevant actions on each Step. This is regardless of whether they are actually aware of the 10 Steps guidance (covered earlier in Section 2.3).
This year, Ipsos engaged Professor Steven Furnell from the University of Nottingham to review how the questionnaire was mapped to the 10 Steps guidance, and suggest a more accurate and robust mapping. The rationale included:
-
ensuring that the Steps are kept mutually exclusive (so an organisation cannot automatically fulfil one step by fulfilling another)
-
setting an appropriately high bar for fulfilling each Step
-
streamlining the mapping.
As a result of this changed mapping, the figures in Table 2.1 are not directly comparable to the equivalent table from previous years. Nevertheless, we have retrospectively applied this new mapping to last year’s results, to allow for a year-on-year comparison. To be clear, the figures in Table 2.1 should not be compared against the equivalent table from last year’s Education Institutions Findings Annex. Where differences against 2022 are shown in the table, these are statistically significant changes using the new mapping.
A notable improvement from last year is with schools when it comes to staff engagement and training (reflected earlier in this section). By contrast, higher education institutions have fallen this year on that same Step, as well as the asset management Step.
Table 2.1: Percentage of organisations undertaking action in each of the 10 Steps areas
| Step description – and how derived from the survey | Primary schools | Secondary schools | Further education colleges | Higher education institutions |
|---|---|---|---|---|
| 1 Risk management – organisations have undertaken a cyber security risk assessment | 48% | 57% | 66% | 87% |
| 2 Engagement and training – organisations have carried out staff training or awareness raising activities | 49% (vs. 42% in 2022) | 62% (vs. 51% in 2022) | 86% | 88% (vs. 100% in 2022) |
| 3 Asset management – organisations have a list of critical assets | 58% | 64% | 70% | 63% (vs. 86% in 2022) |
| 4 Architecture and configuration – organisations have at least three of the following technical rules or controls: up-to-date malware protection, network firewalls, restricted IT admin and access rights, security controls on organisation-owned devices, only allowing access via organisation-owned devices, separate Wi-Fi networks for staff and visitors, specific rules for personal data storage and transfer, or a VPN[footnote 1] | 96% | 99% | 100% | 100% |
| 5 Vulnerability management – organisations have policy to apply software security updates within 14 days | 46% | 60% | 89% | 67% |
| 6 Identity and access management – organisations have any requirement for two-factor authentication when people access the organisation’s network, or for applications they use | 63% | 66% | 86% | 98% |
| 7 Data security – organisations have cloud backups or other kinds of backups | 83% | 67% | 94% | 99% |
| 8 Logging and monitoring – organisations fulfil at least one of the following criteria: using specific tools designed for security monitoring, such as Intrusion Detection Systems, or doing any monitoring of user activity | 78% | 96% | 86% | 98% |
| 9 Incident management – organisations have a formal incident response plan, or at least three of the following: written guidance on who to notify of breaches, roles or responsibilities assigned to specific individuals during or after an incident, external communications and public engagement plans, guidance around when to report incidents externally | 61% | 67% | 66% | 85% |
| 10 Supply chain security – organisations monitor risks from suppliers or their wider supply chain | 30% | 35% | 32% | 52% |
Overall, this table shows that the areas that are less well covered among education institutions continue to be:
-
asset management
-
vulnerability management
-
supply chain security.
Looking at these 10 Steps together, there is still a way to go before these institutions have taken action in all 10 areas, as demonstrated in Figure 2.14. The typical (median) primary school has taken action in 6 of the 10 Steps, the typical secondary school has taken action in 7, the typical college in 8 and the typical higher education institution in 9 of the 10 Steps.
Figure 2.14: Percentage of organisations that have undertaken action in half or all the 10 Steps guidance areas
| Action in half or all the 10 Steps guidance areas | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Undertaken 5 or more of the 10 Steps | 75% | 89% | 91% | 100% | 37% |
| Undertaken all the 10 Steps | 6% | 12% | 14% | 25% | 2% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges; 52 higher education institutions; 2,263 UK businesses
2.8 Cyber crime
Context on cyber crime statistics
The Cyber Security Breaches Survey 2023 covers cyber crime, and the frauds that occur as a result of cyber crime, for the first time. Cyber crime involves gaining unauthorised access, or causing damage, to computers, networks, data or other digital devices, or the information held on those devices. It is defined under the terms of the Computer Misuse Act 1990. Examples of cyber crime include hacking or unauthorised access into online accounts (e.g. banking, email or social media accounts), denial of service attacks, or devices being infected by a virus or other malicious software (including ransomware).
Some of the cyber security breaches and attacks reported in Section 2.1 would not constitute cyber crimes under the above definition. For example, some attempted attacks will not have penetrated an organisation’s cyber defences and some, such as online impersonation, would be beyond the scope of the Computer Misuse Act. Therefore, the statistics here on prevalence differ from the equivalent estimates for all cyber security breaches or attacks (in Section 2.1). They should be considered as a distinct set of figures, specifically for crimes committed against organisations – a subset of all breaches and attacks.
In order to adhere to the Home Office Counting Rules, and avoid double-counting of crimes, we establish if organisations experienced these kinds of cyber incidents as isolated events, or part of a wider chain of events. If they were part of a chain, we have taken the approach of only counting the final event (i.e. type of offence) in the chain.
Finally, cyber crime also facilitates other offences. In recognition of this, we have included questions that capture where cyber crime has led to fraud (i.e. cyber-facilitated fraud). Cyber-facilitated fraud is deception to make a gain, or cause a loss, in relation to money, services, property or goods, which uses data or access obtained through cyber crimes. In these cases, to avoid double-counting, the incident is recorded here as a fraud rather than a cyber crime. We have included these fraud estimates to complement the cyber crime estimates. However, these cyber-facilitated fraud statistics are not intended to capture all frauds committed against education institutions – they only represent the frauds preceded by cyber crimes.
More detail on how these statistics have been arrived at is in the Technical Annex.
Prevalence of cyber crime among education institutions
Figure 2.15 shows a summary of the cyber crime statistics for education institutions. It shows that cyber crime, and the fraud that occurs as a result of cyber crime, tends to be more prevalent in larger education institutions, like colleges and universities.
The main Statistical Release includes, for businesses and charities, further data on the nature, scale and financial impact of cyber crimes. However, this is not possible to report for education institutions, due to sample size limitations.
Figure 2.15: Percentage of organisations that report having experienced the following types of crime at least once in the last 12 months
| Type of crime | Primary schools | Secondary schools | Further education colleges | Higher education institutions | Businesses |
|---|---|---|---|---|---|
| Cyber crime | 12% | 33% | 55% | 52% | 11% |
| Fraud that occurred as a result of cyber crime (cyber-facilitated fraud) | 2% | 3% | 7% | 10% | 3% |
Bases: 241 primary schools; 217 secondary schools; 44 further education colleges;
52 higher education institutions; 2,263 UK businesses
Appendix A: Further information
- The Department for Science, Innovation and Technology and the Home Office would like to thank the following people for their work in the development and carrying out of the survey and for their work compiling the Statistical Release and annexes.
-
Harry Williams, Ipsos
-
Finlay Procter, Ipsos
-
Jamie Douglas, Ipsos
-
Shahil Parmar, Ipsos
-
Nick Coleman, Ipsos
-
Jayesh Navin Shah, Ipsos
-
Professor Steven Furnell, University of Nottingham.
-
The Cyber Security Breaches Survey was first published in 2016 as a research report, and became an Official Statistic in 2017. The previous reports can be found at https://www.gov.uk/government/collections/cyber-security-breaches-survey. This includes the full report and the technical and methodological information for each year.
-
The responsible DSIT analyst for this release is Emma Johns. The responsible statistician is Maddy Ell. For enquiries on this release, from an official statistics perspective, please contact DSIT at [email protected]. As of publication, the DCMS mailbox remains the correct address, but this may change to a DSIT-specific email address next year.
-
For general enquiries contact: 020 7215 1000
-
The Cyber Security Breaches Survey is an official statistics publication and has been produced to the standards set out in the Code of Practice for Official Statistics. For more information, see https://www.statisticsauthority.gov.uk/code-of-practice/. Details of the pre-release access arrangements for this dataset have been published alongside this release.
-
This work was carried out in accordance with the requirements of the international quality standard for Market Research, ISO 20252.
-
Step 4 of the 10 Steps, as mapped to the 2023 survey, cannot be mapped to the 2022 data for a year-on-year comparison, because the questions on separate WiFi networks and VPNs were only asked of half the sample in 2022. ↩
